MEMO in Blockchain: How to Avoid Fraud
4,85
04-24-2025
3487
8 min.
Understanding how MEMO works can help you avoid common scam schemes in the world of cryptocurrency.
Get advice from AML Crypto experts
Imagine you’re transferring cryptocurrency to an exchange address, just like you’ve done dozens of times before. You enter the amount, copy the details, confirm the transaction. Everything seems routine — but the funds never arrive. The support team tells you the transaction was successful, but the money went to someone else. What went wrong?
It turns out, not all blockchains work the same way. On some of them — such as EOS, TLOS, and WAX — you need to include more than just the recipient’s address. There's an extra field called MEMO. This is a string that specifies exactly who the funds are meant for within the platform. Make a mistake — and your money could end up in someone else’s wallet. And if that MEMO was given to you by a scammer, it goes straight into their hands.
This mechanism has become the foundation of numerous scam schemes where funds are not stolen through hacking or phishing, but voluntarily sent by the user — simply because they followed false instructions. In this article, we explain how the MEMO system works, why it can be a security vulnerability, and share real-life cases where money was misdirected — and how we helped uncover what really happened.
It turns out, not all blockchains work the same way. On some of them — such as EOS, TLOS, and WAX — you need to include more than just the recipient’s address. There's an extra field called MEMO. This is a string that specifies exactly who the funds are meant for within the platform. Make a mistake — and your money could end up in someone else’s wallet. And if that MEMO was given to you by a scammer, it goes straight into their hands.
This mechanism has become the foundation of numerous scam schemes where funds are not stolen through hacking or phishing, but voluntarily sent by the user — simply because they followed false instructions. In this article, we explain how the MEMO system works, why it can be a security vulnerability, and share real-life cases where money was misdirected — and how we helped uncover what really happened.
How MEMO Works in Blockchain — and Why It Matters for Secure Crypto Transfers
In account-based blockchain networks like EOS, TLOS, and WAX, cryptocurrency is not sent to unique wallet addresses like in Bitcoin or Ethereum. Instead, transfers are made between accounts with readable names. This means the same platform — such as a crypto exchange — can use a single receiving address for all incoming transactions. To ensure the system assigns the funds to the correct user, the transaction must include an additional field — the MEMO.
Below, you can see how the withdrawal form differs on Bybit when sending crypto via the Bitcoin network versus the EOS network — in the latter case, the MEMO field is mandatory.
Below, you can see how the withdrawal form differs on Bybit when sending crypto via the Bitcoin network versus the EOS network — in the latter case, the MEMO field is mandatory.
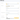
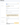
What Is a MEMO in Cryptocurrency Transactions?
A MEMO is a text string embedded in a transaction protocol that acts as an internal recipient identifier on a platform. Imagine an office that receives hundreds of packages every day, all addressed to the same location. To ensure each package reaches the right person, the label includes a room number or employee name. In blockchain transfers, that “room number” is the MEMO. If it's missing or incorrect, the package ends up in the wrong hands — or lost entirely. The same applies to cryptocurrencies: without a correct MEMO, funds may be credited to the wrong user or become irretrievable.
A MEMO is a text string embedded in a transaction protocol that acts as an internal recipient identifier on a platform. Imagine an office that receives hundreds of packages every day, all addressed to the same location. To ensure each package reaches the right person, the label includes a room number or employee name. In blockchain transfers, that “room number” is the MEMO. If it's missing or incorrect, the package ends up in the wrong hands — or lost entirely. The same applies to cryptocurrencies: without a correct MEMO, funds may be credited to the wrong user or become irretrievable.
For example, when transferring tokens to an exchange, the MEMO is your unique user code. Without it, the platform won’t recognize that the transaction was meant for you, and your funds may be lost or stuck in a general holding account.
On a technical level, a MEMO is simply an open text field that you manually fill in when sending a transaction. The blockchain doesn’t verify what you’ve entered, doesn’t tell you if the MEMO is correct, and doesn’t fix your mistakes. It’s all up to the user. That’s exactly why MEMO has become a tool for scammers — they exploit users’ limited understanding of how the system works and easily mislead them. The vulnerability lies not in the technology, but in the lack of knowledge and experience.
How MEMO Is Used in Scam Schemes
One of the main reasons users lose their tokens is a lack of understanding of how MEMO technology works in blockchain systems. At first glance, the transaction process looks familiar: an address, an amount, and a send button. But in certain blockchain networks, a single recipient address can be shared by many users. To distinguish who the transfer is actually meant for, an additional parameter is used — the MEMO. It becomes part of the transaction itself and serves as an internal identifier for the recipient within the system.
Scammers actively exploit this mechanism. Typically, they pose as representatives of a crypto exchange, investment platform, or fund recovery service. The pretext varies — identity verification, refund processing, account recovery, or participation in a promotion. But the scenario is always the same: the victim is instructed to send cryptocurrency to a specific address, accompanied by a mandatory MEMO code.
It’s important to understand that the recipient address often doesn’t raise suspicion — it might belong to a well-known exchange or service. However, the MEMO provided directs the funds not to the user’s account, but straight to the scammer. As a result, the user willingly — and without any external hack — sends their funds to a third party.
What makes this scheme particularly deceptive is that the transaction technically succeeds. There are no errors. From the blockchain’s point of view, everything is valid. So when the user contacts wallet or exchange support, they receive the standard response: “The funds were sent successfully. Refund is not possible.”
These scams remain popular precisely because they don’t appear fraudulent at first glance. The user confirms the transaction, enters the MEMO themselves, and the system simply executes the instructions. Recovering funds in such cases is extremely difficult — especially without technical or legal support.
Scammers actively exploit this mechanism. Typically, they pose as representatives of a crypto exchange, investment platform, or fund recovery service. The pretext varies — identity verification, refund processing, account recovery, or participation in a promotion. But the scenario is always the same: the victim is instructed to send cryptocurrency to a specific address, accompanied by a mandatory MEMO code.
It’s important to understand that the recipient address often doesn’t raise suspicion — it might belong to a well-known exchange or service. However, the MEMO provided directs the funds not to the user’s account, but straight to the scammer. As a result, the user willingly — and without any external hack — sends their funds to a third party.
What makes this scheme particularly deceptive is that the transaction technically succeeds. There are no errors. From the blockchain’s point of view, everything is valid. So when the user contacts wallet or exchange support, they receive the standard response: “The funds were sent successfully. Refund is not possible.”
These scams remain popular precisely because they don’t appear fraudulent at first glance. The user confirms the transaction, enters the MEMO themselves, and the system simply executes the instructions. Recovering funds in such cases is extremely difficult — especially without technical or legal support.
- ✅ Example 1: How It Should Work — A Proper Transfer with MEMOScenario: A user wants to deposit TLOS cryptocurrency to their exchange account.
1.The user logs into their account on the exchange and selects "Deposit TLOS."
2.The exchange provides:- Address: binancetelos
- MEMO: 7628391
4.They send, for example, 20 TLOS to the provided address with the specified MEMO.
5.The exchange automatically recognizes the transaction and credits the funds to the user’s account.
📌 Result: The transfer is successful, and the funds are received. The MEMO allows the system to identify that this specific transaction belongs to that particular user.
- ⛔️ Example 2: How a Scam Scheme Works — Transfer with a “Fake” MEMOScenario: A person receives a message on Telegram from someone claiming to be customer support for their crypto wallet.
1.The scammer says the user’s account has been “blocked” and to unblock it, they must transfer 20 EOS to a “secure” address.
2.The scammer provides:- Address: coinbaseeos1 (a real address belonging to a major exchange)
- MEMO: client_874562 (actually the scammer’s own account identifier)
4.The transaction goes through — the system considers it valid.
5.The user waits for results, but nothing happens. The real platform’s support responds that the funds were sent using the wrong MEMO and cannot be recovered.
📌 Result: The funds were sent to the scammer. Everything looked legitimate, but the MEMO pointed not to the victim’s account, but to the fraudster’s.
Real Case: A Scam Involving a Fake Trading Platform and MEMO Use
A person contacted our company who later became our client. In the initial stage, we conducted a detailed interview, during which we found that he had been drawn into a scam scheme through personal communication with a previously unknown individual. This new “acquaintance” actively encouraged him to participate in what was presented as a reliable and profitable investment platform for cryptocurrency trading.
The platform offered appealing features: a user-friendly interface, supposedly guaranteed returns, and “personal assistance” from specialists who provided guidance on every trade. Everything looked convincing. Seeing the activity and “results,” our client decided to give it a try.
To participate in trading, he was instructed to create a blockchain wallet on the TLOS (Telos) network and transfer funds to it from his exchange account (in this case — Bybit). All transfers required a MEMO — allegedly to link the funds to his profile on the platform. After funding his “trading account,” simulated trading began, showing steady growth and apparent profit.
A few days later, the client decided to withdraw part of the funds. The withdrawal was processed successfully — the funds were returned to the same TLOS wallet. This further reinforced his belief that the platform was legitimate.
The platform offered appealing features: a user-friendly interface, supposedly guaranteed returns, and “personal assistance” from specialists who provided guidance on every trade. Everything looked convincing. Seeing the activity and “results,” our client decided to give it a try.
To participate in trading, he was instructed to create a blockchain wallet on the TLOS (Telos) network and transfer funds to it from his exchange account (in this case — Bybit). All transfers required a MEMO — allegedly to link the funds to his profile on the platform. After funding his “trading account,” simulated trading began, showing steady growth and apparent profit.
A few days later, the client decided to withdraw part of the funds. The withdrawal was processed successfully — the funds were returned to the same TLOS wallet. This further reinforced his belief that the platform was legitimate.

The graph illustrates how funds moved from Bybit [1] to the victim [2], then to the fake trading platform [3], back to the victim’s wallet [4], and finally an attempt to cash out through Bybit [5].
Problems began later, when the client tried to transfer the earned funds back to the exchange in order to convert them into fiat. All attempts to deposit the tokens into his Bybit account failed. The funds were not credited, and error messages appeared. Gradually, the client realized he had been trapped: he was sending real tokens, but receiving fake ones in return — tokens that legitimate exchanges would not accept.
Realizing he had been scammed, the client turned to AML Crypto for assistance.
Realizing he had been scammed, the client turned to AML Crypto for assistance.
- What Actually Happened: A Technical Breakdown of the Incident
After receiving the request, AML Crypto specialists conducted a technical analysis of all transactions and activities related to the scheme. It was discovered that when the client was funding his account on the so-called "trading platform," he was given a specific MEMO to use for the transfer. This MEMO was crafted in such a way that the funds were not sent to the platform, but directly to an account controlled by the scammers.
It was the use of a correctly formatted MEMO that made the transaction appear legitimate on the blockchain level — but in reality, the true recipient was a malicious actor.
It was the use of a correctly formatted MEMO that made the transaction appear legitimate on the blockchain level — but in reality, the true recipient was a malicious actor.

Bholder connection graph illustrating the actual flow of funds — after withdrawal from Bybit, the victim transferred cryptocurrency not to the platform [3], but directly to the scammer [4], who then cashed out the received assets.
The client’s subsequent actions — trading on the platform, recording profits, and withdrawing funds — were no longer taking place on the actual blockchain. All the “transactions” within the platform were carried out using fake tokens that didn’t exist on the blockchain. These tokens were created by the scammers solely within the website interface and had no real value. They merely simulated movement and balance updates, giving the illusion of real trading activity.
Meanwhile, the client’s real tokens had been received by the scammers and were eventually cashed out.
Outcome: Following an investigation conducted by AML Crypto specialists, the fraudulent scheme was confirmed and the full chain of fund movements was reconstructed. We were able to determine that the client's cryptocurrency had been liquidated through a specific crypto exchange, and the funds had passed through identifiable accounts. Transaction analysis and digital footprint correlation allowed us not only to trace the token path but also to identify the ultimate recipient.
Importantly, during the investigation, it was established that the scammer was located in the same country as the victim. This significantly simplified the legal outlook and enabled a transition from a technical investigation to a full-fledged legal process. All collected materials were documented and handed over to the relevant government authorities for further judicial proceedings.
Meanwhile, the client’s real tokens had been received by the scammers and were eventually cashed out.
Outcome: Following an investigation conducted by AML Crypto specialists, the fraudulent scheme was confirmed and the full chain of fund movements was reconstructed. We were able to determine that the client's cryptocurrency had been liquidated through a specific crypto exchange, and the funds had passed through identifiable accounts. Transaction analysis and digital footprint correlation allowed us not only to trace the token path but also to identify the ultimate recipient.
Importantly, during the investigation, it was established that the scammer was located in the same country as the victim. This significantly simplified the legal outlook and enabled a transition from a technical investigation to a full-fledged legal process. All collected materials were documented and handed over to the relevant government authorities for further judicial proceedings.
- Scam Example: Using a Fake MEMO Masquerading as a Cross-Chain Address
In the second case of MEMO-related fraud, our client was deceived while attempting to withdraw EOS from his Bybit exchange account. He intended to transfer the assets to the BNB Smart Chain network for use with a decentralized wallet. However, he didn’t fully understand the technical process of cross-chain transfers and decided to look up instructions online. His search led him to a forum that visually resembled Bybit’s official support page, where a “correct” procedure was being discussed. Shortly afterward, he was contacted via Telegram by someone claiming to be a support agent.
The scammer confidently stated that in order to transfer EOS from the exchange to an external BNB wallet, the client needed to use the “official system deposit address” — bybitdeposit. He explained that all cross-chain transfers are accepted at this address and then automatically rerouted based on the MEMO. This seemed plausible, since the client had previously seen the bybitdeposit address in Bybit’s interface, and he wasn’t entirely familiar with how MEMO works. As a result, the client was fully convinced that he was following a standard withdrawal process.
He proceeded with the transaction: selected EOS as the coin, entered bybitdeposit as the recipient address (as advised), and pasted a BNB address into the MEMO field — the one that, according to the “specialist,” would identify his wallet for receiving funds on the other network. In reality, this address (0x...) had been pre-registered by the scammers in the Bybit system as an identifier for their own account.
The scammer confidently stated that in order to transfer EOS from the exchange to an external BNB wallet, the client needed to use the “official system deposit address” — bybitdeposit. He explained that all cross-chain transfers are accepted at this address and then automatically rerouted based on the MEMO. This seemed plausible, since the client had previously seen the bybitdeposit address in Bybit’s interface, and he wasn’t entirely familiar with how MEMO works. As a result, the client was fully convinced that he was following a standard withdrawal process.
He proceeded with the transaction: selected EOS as the coin, entered bybitdeposit as the recipient address (as advised), and pasted a BNB address into the MEMO field — the one that, according to the “specialist,” would identify his wallet for receiving funds on the other network. In reality, this address (0x...) had been pre-registered by the scammers in the Bybit system as an identifier for their own account.

EOS withdrawal interface on Bybit. The MEMO is obscured — in the actual incident, it contained a cross-chain address supplied by the scammer.
After the transaction was confirmed, the funds were indeed sent to the specified address, and from the blockchain’s perspective, everything appeared valid. However, Bybit’s system credited the assets not to the client’s account, but to another account — one that had been pre-registered by the scammers using the same MEMO (formatted as a BNB address). As a result, the user unknowingly sent funds to the fraudsters — without violating any of the technical withdrawal rules.
When the client realized that the funds never arrived in his BNB wallet, he contacted Bybit’s support team. He was informed that the transaction had been completed successfully and that a refund was not possible. Realizing he had been scammed, the user reached out to AML Crypto for technical analysis, evidence collection, and assistance with the investigation.
Figure: The graph shows how the Bybit client, following a false set of instructions, enters a valid recipient address (bybitdeposit) but an incorrect MEMO — a BNB wallet address provided by the scammer. As a result, the funds are sent not to the expected external BNB wallet, but to an internal account controlled by the scammer, registered with that specific MEMO.
The graph highlights the discrepancy between the intended transfer route (Bybit → victim’s BNB wallet) and the actual route taken (Bybit → scammer’s internal account).
When the client realized that the funds never arrived in his BNB wallet, he contacted Bybit’s support team. He was informed that the transaction had been completed successfully and that a refund was not possible. Realizing he had been scammed, the user reached out to AML Crypto for technical analysis, evidence collection, and assistance with the investigation.
Figure: The graph shows how the Bybit client, following a false set of instructions, enters a valid recipient address (bybitdeposit) but an incorrect MEMO — a BNB wallet address provided by the scammer. As a result, the funds are sent not to the expected external BNB wallet, but to an internal account controlled by the scammer, registered with that specific MEMO.
The graph highlights the discrepancy between the intended transfer route (Bybit → victim’s BNB wallet) and the actual route taken (Bybit → scammer’s internal account).

Bholder connection graph illustrating the flow of cryptocurrency in the described incident.
How to Protect Yourself from These Schemes
Scam tactics involving MEMO are becoming increasingly sophisticated, and their true power lies not in technical tricks, but in the fact that many users simply don’t understand how the system works. To avoid becoming a victim, it’s important not only to stay vigilant, but also to understand the basic principles of crypto transfers. Here are a few key rules to help you stay safe:
Understand how transfers work and what MEMO means. If you use exchanges, blockchain wallets, or send crypto, it’s essential to know which parameters affect the transaction. MEMO is not a random field — it’s a critical component. Spend 10 minutes learning how your specific network works — it could significantly reduce your risk.
Verify your sources of information. Don’t trust messages in Telegram, WhatsApp, or social media, even if they appear to be from customer support. Legitimate exchange representatives will never message you first via messengers.
Always double-check the address and MEMO manually. Only copy them directly from the official interface of your exchange or wallet. Never use details from emails, chats, or third-party websites.
Avoid sending funds to platforms lacking transparency. If a project has no legal information, clear terms of use, or reliable customer support — that’s a red flag. Real companies don’t hide their identity.
Be extra cautious with investment offers. If someone promises guaranteed returns, entry bonuses, or refund guarantees — it’s likely a scam. In the crypto world, there’s no such thing as easy or risk-free money.
❗️If you suspect you’ve been scammed, don’t wait. Time is critical. The sooner you act, the better the chances of tracing transactions and taking appropriate action.
Reach out to the experts at AML Crypto — our team provides professional assistance in tracing lost funds, identifying transaction trails, and preparing documentation that can be used in legal proceedings.
Reach out to the experts at AML Crypto — our team provides professional assistance in tracing lost funds, identifying transaction trails, and preparing documentation that can be used in legal proceedings.
- You can contact us:
- On Telegram: https://t.me/AMLCrypto
- Via email: info@amlcrypto.io
Conclusion
The MEMO field is just a simple string within a transaction — but it’s the key element that determines who receives the funds. In account-based blockchains like EOS, TLOS, and WAX, MEMO is a required component. Not understanding its purpose, trusting “support” messages in chat apps, or copying instructions from unreliable sources can easily lead to a complete loss of crypto assets.
Scammers don’t hack wallets or spoof addresses — they exploit users’ lack of knowledge. And because such transactions are technically valid, exchanges and wallets typically bear no responsibility for the consequences.
If you’ve already fallen into one of these traps, it’s important not to delay the investigation. The sooner a technical analysis begins, the higher the chance of tracing the assets, securing digital evidence, and forwarding the case to the proper authorities in time.
AML Crypto offers assistance in these situations — from analyzing blockchain transactions to compiling evidence and preparing documentation for legal proceedings.
Scammers don’t hack wallets or spoof addresses — they exploit users’ lack of knowledge. And because such transactions are technically valid, exchanges and wallets typically bear no responsibility for the consequences.
If you’ve already fallen into one of these traps, it’s important not to delay the investigation. The sooner a technical analysis begins, the higher the chance of tracing the assets, securing digital evidence, and forwarding the case to the proper authorities in time.
AML Crypto offers assistance in these situations — from analyzing blockchain transactions to compiling evidence and preparing documentation for legal proceedings.
Want to learn more and get expert advice? Leave your email and we will contact you promptly!
Check blockchain address using Btrace
In seconds, determine the risk level of the counterparty’s address, find out the source of his funds and make an informed decision about interacting with him.

PREVENT FUNDS BLOCKING

PROTECT YOURSELF FROM SCAMMERS

AVOID TROUBLE WITH THE LAW
We also recommend














