Event chronology
Get advice from AML Crypto experts
Source : https://t.me/Bybit_exploit

On 2025-02-21 at 14:16:11 (UTC), the Bybit cryptocurrency exchange faced a major hacker attack. The attackers gained access to one of the platform's cold wallets and withdrew 401,346 ETH, as well as 113,375.548 synthetic ETH (including 15,000 cmETH, 90,375 stETH, 8,000 mETH) and 90 USDT. At the time of the theft, the total equivalent of the stolen funds exceeded 1.4 billion US dollars.
Bybit exchange address: 0x1Db92e2EeBC8E0c075a02BeA49a2935BcD2dFCF4
Exploiter address: 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2
Theft transactions:
0xb61413c495fdad6114a7aa863a00b2e3c28945979a10885b12b30316ea9f072c
(401,346 ETH)
0xa284a1bc4c7e0379c924c73fcea1067068635507254b03ebbbd3f4e222c1fae0
(90,375 stETH)
0x847b8403e8a4816a4de1e63db321705cdb6f998fb01ab58f653b863fda988647
(15,000 cmETH)
0xbcf316f5835362b7f1586215173cc8b294f5499c60c029a3de6318bf25ca7b20
(8000 mETH)
0x25800d105db4f21908d646a7a3db849343737c5fba0bc5701f782bf0e75217c9
(90 USDT)
Number of attacker addresses at a given time: 1
P.S. The attacker didn't even leave the 90 USDT that were at the address. As they say, 90 dollars are never too much 🙂
Bybit is one of the largest cryptocurrency exchanges, founded in 2018, operating in more than 195 countries. As of 2025, the number of users of the platform has exceeded 60 million, making it the second largest crypto exchange in the world. Bybit's average daily trading volume exceeds $36 billion, and the total amount of reserves is estimated in the range of $10.95-20 billion according to various estimates.
Bybit exchange address: 0x1Db92e2EeBC8E0c075a02BeA49a2935BcD2dFCF4
Exploiter address: 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2
Theft transactions:
0xb61413c495fdad6114a7aa863a00b2e3c28945979a10885b12b30316ea9f072c
(401,346 ETH)
0xa284a1bc4c7e0379c924c73fcea1067068635507254b03ebbbd3f4e222c1fae0
(90,375 stETH)
0x847b8403e8a4816a4de1e63db321705cdb6f998fb01ab58f653b863fda988647
(15,000 cmETH)
0xbcf316f5835362b7f1586215173cc8b294f5499c60c029a3de6318bf25ca7b20
(8000 mETH)
0x25800d105db4f21908d646a7a3db849343737c5fba0bc5701f782bf0e75217c9
(90 USDT)
Number of attacker addresses at a given time: 1
P.S. The attacker didn't even leave the 90 USDT that were at the address. As they say, 90 dollars are never too much 🙂
Bybit is one of the largest cryptocurrency exchanges, founded in 2018, operating in more than 195 countries. As of 2025, the number of users of the platform has exceeded 60 million, making it the second largest crypto exchange in the world. Bybit's average daily trading volume exceeds $36 billion, and the total amount of reserves is estimated in the range of $10.95-20 billion according to various estimates.
On 2025-02-21 at 14:16:11 (UTC), the Bybit cryptocurrency exchange faced a major hacker attack. The attackers gained access to one of the platform's cold wallets and withdrew 401,346 ETH, as well as 113,375.548 synthetic ETH (including 15,000 cmETH, 90,375 stETH, 8,000 mETH) and 90 USDT. At the time of the theft, the total equivalent of the stolen funds exceeded 1.4 billion US dollars.
Bybit exchange address: 0x1Db92e2Ee
BC8E0c075a02BeA49a2935BcD2dFCF4
Exploiter address: 0x47666Fab8bd0Ac
7003bce3f5C3585383F09486E2
Транзакции кражи:
9f072c
(401,346 ETH)
fae0
(90,375 stETH)
647
(15,000 cmETH)
a7b20
(8000 mETH)
5217c9
(90 USDT)
Number of attacker addresses at a given time: 1
P.S. The attacker didn't even leave the 90 USDT that were at the address. As they say, 90 dollars are never too much 🙂
Bybit is one of the largest cryptocurrency exchanges, founded in 2018, operating in more than 195 countries. As of 2025, the number of users of the platform has exceeded 60 million, making it the second largest crypto exchange in the world. Bybit's average daily trading volume exceeds $36 billion, and the total amount of reserves is estimated in the range of $10.95-20 billion according to various estimates.
Bybit exchange address: 0x1Db92e2Ee
BC8E0c075a02BeA49a2935BcD2dFCF4
Exploiter address: 0x47666Fab8bd0Ac
7003bce3f5C3585383F09486E2
Транзакции кражи:
- 0xb61413c495fdad6114a7aa863a0
9f072c
(401,346 ETH)
- 0xa284a1bc4c7e0379c924c73fcea1
fae0
(90,375 stETH)
- 0x847b8403e8a4816a4de1e63db321
647
(15,000 cmETH)
- 0xbcf316f5835362b7f1586215173c
a7b20
(8000 mETH)
- 0x25800d105db4f21908d646a7a3d
5217c9
(90 USDT)
Number of attacker addresses at a given time: 1
P.S. The attacker didn't even leave the 90 USDT that were at the address. As they say, 90 dollars are never too much 🙂
Bybit is one of the largest cryptocurrency exchanges, founded in 2018, operating in more than 195 countries. As of 2025, the number of users of the platform has exceeded 60 million, making it the second largest crypto exchange in the world. Bybit's average daily trading volume exceeds $36 billion, and the total amount of reserves is estimated in the range of $10.95-20 billion according to various estimates.
Bybit Hack: Inside the $1.4B Theft
Bybit has different types of wallets, including hot and cold wallets for storing funds. Periodically, Bybit employees rebalance funds between them. On 2025-02-21, Bybit employees did this. But as a result, all funds were withdrawn from the Bybit cold wallet without authorization.
This address uses multi-signature, which means that multiple keys must be signed to complete a transaction. In Bybit's case, the keys were owned by different people for security purposes. The wallet is managed through the Safe interface.
Gnosis Safe (now Safe) is a multisig wallet for secure storage and management of crypto assets.
To successfully complete a transaction at this address, signatures from 3 out of 6 signatories were required. Having initiated a normal transaction to transfer funds from a cold wallet, the transaction was signed by all three participants in the site interface and confirmed by each on their device.
However, as a result, a different transaction was sent to the network, and not the one shown in the safe.global site interface. This unauthorized transaction allowed the attackers to gain control over the cold wallet.
There was probably a visual substitution of data in the web interface when signing the transaction.
This address uses multi-signature, which means that multiple keys must be signed to complete a transaction. In Bybit's case, the keys were owned by different people for security purposes. The wallet is managed through the Safe interface.
Gnosis Safe (now Safe) is a multisig wallet for secure storage and management of crypto assets.
To successfully complete a transaction at this address, signatures from 3 out of 6 signatories were required. Having initiated a normal transaction to transfer funds from a cold wallet, the transaction was signed by all three participants in the site interface and confirmed by each on their device.
However, as a result, a different transaction was sent to the network, and not the one shown in the safe.global site interface. This unauthorized transaction allowed the attackers to gain control over the cold wallet.
There was probably a visual substitution of data in the web interface when signing the transaction.
How did the hack happen?

2025-02-21 at 15:20 ZachXBT publishes information on his Telegram channel about suspicious outgoing transactions worth $1.46 billion+ from addresses belonging to ByBit
Number of attacker addresses at a given time: 4
Number of attacker addresses at a given time: 4
Detection of a suspicious event by blockchain researcher Zach

2025-02-21 15:44 (UTC) In his post on Platform X, Bybit CEO Ben Zhou reports an unauthorized transfer of funds. Calls on analytics teams to help track the funds.
Number of attacker addresses at a given time: 4
Number of attacker addresses at a given time: 4
Bybit CEO Ben Zhou’s reaction

2025-02-21 14:43 (UTC) the attacker starts withdrawing USDT, mETH, stETH, cmETH tokens to a separate blockchain address and then exchanges them for ETH. For the exchange, he uses DEX Uniswap, ParaSwap, Dodo.
Number of attacker addresses at a given time: 4
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Summary of services:
- ParaSwap is a liquidity aggregator that searches for the best token swap rates by routing orders between different DEXs.
- Uniswap is the largest decentralized exchange (DEX) that uses an automated market maker (AMM) to swap tokens without intermediaries.
- Dodo is a DEX powered by a **Proactive Market Maker (PMM)** mechanism, which provides lower slippage and optimized pricing compared to classic AMMs.
Number of attacker addresses at a given time: 4
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Summary of services:
- ParaSwap is a liquidity aggregator that searches for the best token swap rates by routing orders between different DEXs.
- Uniswap is the largest decentralized exchange (DEX) that uses an automated market maker (AMM) to swap tokens without intermediaries.
- Dodo is a DEX powered by a **Proactive Market Maker (PMM)** mechanism, which provides lower slippage and optimized pricing compared to classic AMMs.
Swaps of stolen synthetic tokens and USDT via DEX
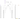
2025-02-21 15:48 the attacker starts to scatter funds across multiple addresses
Number of attacker addresses at a given time: 44
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Number of attacker addresses at a given time: 44
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Initial distribution of stolen funds

2025-02-21 at 17:15 A post with a live broadcast was [published] on the official Bybit X page, in which Bybit CEO Ben Zhou comments on the situation.
Introduction and Overview:
Ben Zhou started the live stream by explaining the current situation and thanking the viewers for tuning in. He mentioned that ByBit is going through a very challenging time after the hack of their Ethereum wallet. The incident occurred about two hours ago. Ben stated that the live stream would provide updates and answer questions from the community.
How the Incident Happened:
- ByBit uses a cold and hot wallet system for managing funds. When the balance in the hot wallet reaches a certain threshold, funds are transferred from the cold wallet to the hot wallet.
- During a routine transfer from the cold wallet to the hot wallet, the transaction was carried out using a multisig (multi-signature) system through the Safe service. This system requires multiple signers to approve the transaction.
- At the time of signing, Ben, being the last signer, verified the URL and destination address using the official Safe website. He also used a Ledger device to sign the transaction.
- About 30 minutes after signing, Ben received an emergency call that the wallet had been drained — the funds were stolen.
Details of the Hack:
- Hackers managed to manipulate the signing interface, possibly by compromising the computers of all the signers or exploiting a vulnerability in the Safe service. While Ben was confident they were using the correct URL and destination address, it’s possible that the hackers altered the transaction data at the smart contract level.
- Ben emphasized that Ethereum uses smart contracts, which can be more vulnerable to manipulation, and this vulnerability was likely exploited in the hack of ByBit’s Ethereum wallet.
Size of the Damage:
- Around 401,000 ETH was stolen. This affected only the Ethereum wallet, and no other assets or wallets were compromised.
- According to Ben, other wallets holding assets like Bitcoin or USDT were not affected by this incident.
- Despite the loss, the company is actively working to mitigate the consequences and recover the stolen funds.
Current Situation with Withdrawals:
- ByBit continues to process withdrawal requests, but the number of requests has increased significantly over the past few hours, causing delays.
- At the moment, withdrawals remain open, but some large requests require additional verification from the security team.
- Importantly, despite the high load, the company is still paying out funds and overall 70% of withdrawal requests have already been processed.
Answers to Client Questions:
- Ben guaranteed that customer funds are safe, as ByBit adheres to a 1:1 principle on reserves.
- Ben noted that despite the theft of funds from the Ethereum wallet, the company has enough reserves to cover losses from its coffers if needed.
- Question about possible compensation for the stolen funds: ByBit plans to reach out to partners and use its reserve fund to cover losses if the funds cannot be recovered.
Investigation and Security Measures:
- ByBit is working with the security team and law enforcement to recover the stolen funds and find out the details of the hack.
- An investigation is currently underway and the team is working with external specialists to trace the stolen funds and possibly recover them through centralised exchanges or other channels.
- Ben said ByBit's security team is scrutinising all other wallets to make sure there are no other vulnerabilities. So far, only the Ethereum wallet has been compromised.
Recovery Efforts and Security Enhancements:
- To address the liquidity issue with Ethereum, ByBit is securing a bridge loan from partners to cover the deficit and ensure the continuation of withdrawals.
- Ben clarified that ByBit is not buying Ethereum on the market but is relying on bridge loans to resolve the liquidity crunch.
- Additionally, ByBit is working with the Safe team to understand what happened and identify any weaknesses in their security protocols.
Follow-up on Client Questions:
- Ben responded to concerns about whether ByBit would be able to recover the stolen Ethereum. He confirmed that the company is actively working with partners and authorities to track and recover the stolen funds. However, the amount is large, and the recovery may take time.
- Withdrawals for tokens other than Ethereum are unaffected, and all other services are functioning as usual.
Conclusion:
- Despite the hack, Ben Zhou reassured the community that ByBit will continue operating, and clients’ funds will be protected. He thanked partners and clients for their support and assured everyone that ByBit is committed to transparency and restoring trust.
- The company is investigating the incident, and more updates will be provided as the situation unfolds.
- ByBit plans to conduct a thorough review of its security procedures and implement necessary improvements to prevent such incidents in the future.
Number of attacker addresses at the moment: 44
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Introduction and Overview:
Ben Zhou started the live stream by explaining the current situation and thanking the viewers for tuning in. He mentioned that ByBit is going through a very challenging time after the hack of their Ethereum wallet. The incident occurred about two hours ago. Ben stated that the live stream would provide updates and answer questions from the community.
How the Incident Happened:
- ByBit uses a cold and hot wallet system for managing funds. When the balance in the hot wallet reaches a certain threshold, funds are transferred from the cold wallet to the hot wallet.
- During a routine transfer from the cold wallet to the hot wallet, the transaction was carried out using a multisig (multi-signature) system through the Safe service. This system requires multiple signers to approve the transaction.
- At the time of signing, Ben, being the last signer, verified the URL and destination address using the official Safe website. He also used a Ledger device to sign the transaction.
- About 30 minutes after signing, Ben received an emergency call that the wallet had been drained — the funds were stolen.
Details of the Hack:
- Hackers managed to manipulate the signing interface, possibly by compromising the computers of all the signers or exploiting a vulnerability in the Safe service. While Ben was confident they were using the correct URL and destination address, it’s possible that the hackers altered the transaction data at the smart contract level.
- Ben emphasized that Ethereum uses smart contracts, which can be more vulnerable to manipulation, and this vulnerability was likely exploited in the hack of ByBit’s Ethereum wallet.
Size of the Damage:
- Around 401,000 ETH was stolen. This affected only the Ethereum wallet, and no other assets or wallets were compromised.
- According to Ben, other wallets holding assets like Bitcoin or USDT were not affected by this incident.
- Despite the loss, the company is actively working to mitigate the consequences and recover the stolen funds.
Current Situation with Withdrawals:
- ByBit continues to process withdrawal requests, but the number of requests has increased significantly over the past few hours, causing delays.
- At the moment, withdrawals remain open, but some large requests require additional verification from the security team.
- Importantly, despite the high load, the company is still paying out funds and overall 70% of withdrawal requests have already been processed.
Answers to Client Questions:
- Ben guaranteed that customer funds are safe, as ByBit adheres to a 1:1 principle on reserves.
- Ben noted that despite the theft of funds from the Ethereum wallet, the company has enough reserves to cover losses from its coffers if needed.
- Question about possible compensation for the stolen funds: ByBit plans to reach out to partners and use its reserve fund to cover losses if the funds cannot be recovered.
Investigation and Security Measures:
- ByBit is working with the security team and law enforcement to recover the stolen funds and find out the details of the hack.
- An investigation is currently underway and the team is working with external specialists to trace the stolen funds and possibly recover them through centralised exchanges or other channels.
- Ben said ByBit's security team is scrutinising all other wallets to make sure there are no other vulnerabilities. So far, only the Ethereum wallet has been compromised.
Recovery Efforts and Security Enhancements:
- To address the liquidity issue with Ethereum, ByBit is securing a bridge loan from partners to cover the deficit and ensure the continuation of withdrawals.
- Ben clarified that ByBit is not buying Ethereum on the market but is relying on bridge loans to resolve the liquidity crunch.
- Additionally, ByBit is working with the Safe team to understand what happened and identify any weaknesses in their security protocols.
Follow-up on Client Questions:
- Ben responded to concerns about whether ByBit would be able to recover the stolen Ethereum. He confirmed that the company is actively working with partners and authorities to track and recover the stolen funds. However, the amount is large, and the recovery may take time.
- Withdrawals for tokens other than Ethereum are unaffected, and all other services are functioning as usual.
Conclusion:
- Despite the hack, Ben Zhou reassured the community that ByBit will continue operating, and clients’ funds will be protected. He thanked partners and clients for their support and assured everyone that ByBit is committed to transparency and restoring trust.
- The company is investigating the incident, and more updates will be provided as the situation unfolds.
- ByBit plans to conduct a thorough review of its security procedures and implement necessary improvements to prevent such incidents in the future.
Number of attacker addresses at the moment: 44
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Ben Zhou Live Stream

2025-02-21 19:09 Arham [stated] that ZachXBT provided Arham with the evidence it collected that Lazarus Group is behind the incident. The data has been forwarded to Bybit.
Number of attacker addresses at the moment: 44
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Number of attacker addresses at the moment: 44
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Lazarus Group is behind Bybit Hack incident, according to ZachXBT

2025-02-21 23:59 UTC Following the results of the first day, AMLcrypto.io published an analysis of the movement of stolen assets through transit addresses, the use of Uniswap, ParaSwap, Dodo.
🟣 - Bybit exchange address hacked [13], decentralized exchange addresses [23-26]
⚫️ - Exploiter addresses
Number of attacker addresses at the time: 44
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
🟣 - Bybit exchange address hacked [13], decentralized exchange addresses [23-26]
⚫️ - Exploiter addresses
Number of attacker addresses at the time: 44
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Results of blockchain transaction analysis from AMLcrypto team


2025-02-22 at 06:22:31 on the Bitcointalk forum, a Bybit employee publishes a screenshot of the correspondence with a Bybit representative regarding this incident. A screenshot of a letter from Bybit is provided asking Exch to assist in this incident, since the transfer of part of the funds to the Exch crypto exchanger
In response to Bybit's message, exch points out the problem it had previously encountered, that its users' funds were blocked on the exch exchange. It is specified why Bybit believes that exch will help?!
eXch — is an automatic cryptocurrency exchanger that allows users to exchange various cryptocurrencies without registration. The platform supports fast exchanges and provides an API for integration.
Number of attacker addresses at the time: 44
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
In response to Bybit's message, exch points out the problem it had previously encountered, that its users' funds were blocked on the exch exchange. It is specified why Bybit believes that exch will help?!
eXch — is an automatic cryptocurrency exchanger that allows users to exchange various cryptocurrencies without registration. The platform supports fast exchanges and provides an API for integration.
Number of attacker addresses at the time: 44
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Details of Exch's refusal to help Bybit


2022-02-22 07:04:11 (UTC) the attacker transferred funds to deposit addresses of the ChainFlip service. According to the service explorer data, the funds were sent to the address bc1qlu4a33zjspefa3tnq566xszcr0fvwz05ewhqfq on the Bitcoin network.
Chainflip is a decentralized cross-chain protocol that allows users to exchange native crypto assets between different blockchains (e.g. Bitcoin, Ethereum, Solana) without wrapped tokens and centralized intermediaries.
Data source in screenshot 1: https://scan.chainflip.io/swaps
The designations on the transaction graph are:
🟣 - Bybit exchange address subjected to hacking [1], Chainflip addresses [7-10]
⚫️ - Ethereum network exploiter addresses [2-6], Bitcoin network exploiter addresses [11-15].
Number of attacker addresses at the time: 58
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Chainflip is a decentralized cross-chain protocol that allows users to exchange native crypto assets between different blockchains (e.g. Bitcoin, Ethereum, Solana) without wrapped tokens and centralized intermediaries.
Data source in screenshot 1: https://scan.chainflip.io/swaps
The designations on the transaction graph are:
🟣 - Bybit exchange address subjected to hacking [1], Chainflip addresses [7-10]
⚫️ - Ethereum network exploiter addresses [2-6], Bitcoin network exploiter addresses [11-15].
Number of attacker addresses at the time: 58
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
2022-02-22 07:04:11 (UTC) the attacker transferred funds to deposit addresses of the ChainFlip service. According to the service explorer data, the funds were sent to the address bc1qlu4a33zjspefa3tnq566xszcr0fvwz
05ewhqfq on the Bitcoin network.
Chainflip is a decentralized cross-chain protocol that allows users to exchange native crypto assets between different blockchains (e.g. Bitcoin, Ethereum, Solana) without wrapped tokens and centralized intermediaries.
Data source in screenshot 1: https://scan.chainflip.io/swaps
The designations on the transaction graph are:
🟣 - Bybit exchange address subjected to hacking [1], Chainflip addresses [7-10]
⚫️ - Ethereum network exploiter addresses [2-6], Bitcoin network exploiter addresses [11-15].
Number of attacker addresses at the time: 58
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
05ewhqfq on the Bitcoin network.
Chainflip is a decentralized cross-chain protocol that allows users to exchange native crypto assets between different blockchains (e.g. Bitcoin, Ethereum, Solana) without wrapped tokens and centralized intermediaries.
Data source in screenshot 1: https://scan.chainflip.io/swaps
The designations on the transaction graph are:
🟣 - Bybit exchange address subjected to hacking [1], Chainflip addresses [7-10]
⚫️ - Ethereum network exploiter addresses [2-6], Bitcoin network exploiter addresses [11-15].
Number of attacker addresses at the time: 58
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Withdrawal of part of funds via ChainFlip





2025-02-22 15:10 UTC Arham reported that he has found a link between the blockchain addresses used in the ByBit and Phemex hacks, which may indicate that the same hacker was involved in both incidents.
This confirms the involvement of Lazarus Group, as this hacker group has previously used similar attack methods and money laundering schemes to those seen in the ByBit and Phemex hacks.
Number of attacker addresses at the time: 557
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
This confirms the involvement of Lazarus Group, as this hacker group has previously used similar attack methods and money laundering schemes to those seen in the ByBit and Phemex hacks.
Number of attacker addresses at the time: 557
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Arkham Confirms Lazarus Group Tie-in
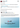
2025-02-22 at 15:22 mETH Protocol reports successful locking and return of $15,000 cmETH, as announced in a post on Platform X.
mETH Protocol is a liquid Ethereum staking platform created by the Mantle community. Users can stake ETH and receive $mETH in return, which generates income and can be used in DeFi applications. If necessary, it can be exchanged back for ETH, taking into account the accumulated rewards.
Number of attacker addresses at a given time: 573
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
mETH Protocol is a liquid Ethereum staking platform created by the Mantle community. Users can stake ETH and receive $mETH in return, which generates income and can be used in DeFi applications. If necessary, it can be exchanged back for ETH, taking into account the accumulated rewards.
Number of attacker addresses at a given time: 573
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Blocking and returning stolen 15,000 cmETH thanks to mETH Protoco


2025-02-22 at 16:43 SlowMist published an article in which it claimed to have found evidence of possible involvement of Lazarus Group in the Bybit hack. SlowMist found identical addresses and other evidence pointing to similar attack patterns.
In September 2024, Singapore-based cryptocurrency exchange BingX was hacked, resulting in over $43 million being stolen from hot wallets. The stolen assets included Ethereum (ETH), Binance Coin (BNB), and Tether (USDT).
In January 2025, Singapore-based cryptocurrency exchange Phemex was hacked, resulting in approximately $85 million being stolen from hot wallets.
Some security experts have suggested that the North Korean-linked hacking group Lazarus may be behind both attacks, based on the tactics used.
Number of attacker addresses at a given time: 751
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
In September 2024, Singapore-based cryptocurrency exchange BingX was hacked, resulting in over $43 million being stolen from hot wallets. The stolen assets included Ethereum (ETH), Binance Coin (BNB), and Tether (USDT).
In January 2025, Singapore-based cryptocurrency exchange Phemex was hacked, resulting in approximately $85 million being stolen from hot wallets.
Some security experts have suggested that the North Korean-linked hacking group Lazarus may be behind both attacks, based on the tactics used.
Number of attacker addresses at a given time: 751
API to get blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
SlowMist Confirms Link to Lazarus Group

Cryptocurrency exchange Bybit has launched a recovery bounty program for the recovery of stolen funds following a recent hack. The initiative offers rewards of up to 10% of the recovered amount to cybersecurity specialists and blockchain analysts who help track down and recover the stolen assets. In the event of a full recovery of funds, the total reward amount could reach $140 million. Bybit emphasizes that this move is aimed at enhancing security and protecting users of the platform.
Number of attacker addresses at the time: 607
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Number of attacker addresses at the time: 607
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Bybit Offers Rewards Up to $140 Million for Help in Recovering Stolen Funds

ChangeNOW is a non-custodial, instant cryptocurrency exchange service that supports over 850 digital assets and operates without registration. The platform allows users to exchange cryptocurrency without limits and storage, providing fast and anonymous transactions.
THORChain is a decentralized liquidity protocol that allows users to exchange crypto assets between different blockchains without the need for centralized exchanges or wrapped tokens.
Number of attacker addresses at the time: 884
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
THORChain is a decentralized liquidity protocol that allows users to exchange crypto assets between different blockchains without the need for centralized exchanges or wrapped tokens.
Number of attacker addresses at the time: 884
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
AMLcrypto.io published an investigation summary with 884 attacker blockchain addresses. Interactions with ChangeNow, ThorChain were identified.
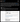
2025-02-23 at 4:32 UTC In the post, Ben Zhou called on eXch to provide assistance, since this is not about the relationship between the two companies, but a common confrontation with the attackers. He also emphasized that Interpol and other international regulatory bodies are handling the case.
Number of attacker addresses at the time: 995
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Number of attacker addresses at the time: 995
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Bybit CEO Ben Zhou responded to the published correspondence between Bybit and eXch

Tether. Tether Limited is the issuer of the USDT stablecoin, pegged to the US dollar. Founded in 2014, Tether provides users with the ability to transact in digital assets while minimizing the volatility associated with other cryptocurrencies.
FixedFloat is a non-custodial automated service for instant cryptocurrency exchange, launched in 2018. The platform supports over 60 digital assets, including Bitcoin, Ethereum, Tether, and Monero, and allows users to exchange them without registration and KYC procedures.
Avax. Avalanche is a smart contract platform for decentralized applications and its native token AVAX. Launched in September 2020 by Ava Labs, a Cornell alumni company, Avalanche enables the creation of feature-rich blockchains and dApps while ensuring high scalability and cross-chain compatibility.
Coinex. CoinEx is an international cryptocurrency exchange founded in 2017, providing users in over 200 countries with convenient access to digital asset trading.
Bitget. Bitget is a centralized cryptocurrency exchange founded in 2018 and registered in the Seychelles.
Circle. Circle Internet Financial Limited is a financial technology company founded in October 2013 by Jeremy Allaire and Sean Neville. The company operates the USDC stablecoin, whose value is pegged to the US dollar. Circle is headquartered in Boston, Massachusetts.
Number of attacker addresses at the time: 1 450
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
FixedFloat is a non-custodial automated service for instant cryptocurrency exchange, launched in 2018. The platform supports over 60 digital assets, including Bitcoin, Ethereum, Tether, and Monero, and allows users to exchange them without registration and KYC procedures.
Avax. Avalanche is a smart contract platform for decentralized applications and its native token AVAX. Launched in September 2020 by Ava Labs, a Cornell alumni company, Avalanche enables the creation of feature-rich blockchains and dApps while ensuring high scalability and cross-chain compatibility.
Coinex. CoinEx is an international cryptocurrency exchange founded in 2017, providing users in over 200 countries with convenient access to digital asset trading.
Bitget. Bitget is a centralized cryptocurrency exchange founded in 2018 and registered in the Seychelles.
Circle. Circle Internet Financial Limited is a financial technology company founded in October 2013 by Jeremy Allaire and Sean Neville. The company operates the USDC stablecoin, whose value is pegged to the US dollar. Circle is headquartered in Boston, Massachusetts.
Number of attacker addresses at the time: 1 450
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
2025-02-23 at 15:41 Bybit reported successfully freezing $42.89 million in a day.

Number of attacker addresses at the time: 2 291
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
2025-02-24 13:00 UTC. Elliptic published an article claiming that the attackers have already laundered 14.5% of the stolen assets, which currently amounts to $195 million. Elliptic suggests that they may have used mixers to do this. The report also notes that eXch has refused to cooperate with the investigation.
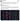
2025-02-25-25 2:07 Ben Zhou announced something in the next few days that will allow the entire industry to fight hackers and solve the problem of recovering stolen funds.
Number of attacker addresses at the time: 4 153
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklis
Number of attacker addresses at the time: 4 153
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklis
Ben Zhou: Let's introduce something to protect against hackers and solve the problem of recovering stolen assets
Chainalysis analyzes the attack methods in a blog post, pointing out similarities to tactics previously used by hackers linked to North Korea. The article highlights the importance of transparency and cooperation in the crypto industry to track and recover stolen funds, as well as to strengthen collective security against such threats.
Number of attacker addresses at the time: 4 181
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Number of attacker addresses at the time: 4 181
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Chainalysis and Bybit Collaboration
Lazarus Group is one of the most notorious and dangerous hacker groups in the world, believed to be linked to the North Korean government (DPRK). The group specializes in cyber espionage, cyberattacks on financial institutions, and the development of malicious software.
Group Objectives:
- Funding the DPRK regime through cybercrime.
- Sabotaging and disrupting enemy infrastructure.
- Conducting industrial and military espionage operations.
Key Attacks:
- Sony Pictures Attack (2014)
Lazarus Group is attributed with the cyberattack on Sony Pictures Entertainment in response to the release of The Interview, a film satirizing the assassination of North Korean leader Kim Jong-un.
- WannaCry Campaign (2017)
The spread of the WannaCry ransomware worm, which infected over 200,000 computers across 150 countries.
- Bank Heists via SWIFT (2016 – Present)
In 2016, hackers targeted the Central Bank of Bangladesh, attempting to steal $1 billion through the SWIFT system but managed to withdraw "only" $81 million.
- Cryptocurrency Theft (2018 – Present)
One of the most high-profile attacks was the 2022 hack of the Ronin Network bridge, resulting in the theft of $600 million.
Attack Methods:
- Phishing and Social Engineering (e.g., attacks through fake job offers targeting IT specialists).
- Use of Malicious Software (e.g., Remote Access Trojans – RATs).
- Exploitation of Software Vulnerabilities.
Record-Breaking Thefts and Increased Activity in 2024–2025
Hackers affiliated with North Korea stole approximately $660.5 million across 20 incidents in 2023. In 2024, this amount surged to $1.34 billion across 47 incidents—a 102.88% increase compared to the previous year. The Bybit hack alone resulted in a stolen sum that exceeded the total amount stolen by North Korea throughout 2024 by nearly $160 million.
Number of attacker addresses at the time: 4 876 (2025-02-25 12:35)
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Group Objectives:
- Funding the DPRK regime through cybercrime.
- Sabotaging and disrupting enemy infrastructure.
- Conducting industrial and military espionage operations.
Key Attacks:
- Sony Pictures Attack (2014)
Lazarus Group is attributed with the cyberattack on Sony Pictures Entertainment in response to the release of The Interview, a film satirizing the assassination of North Korean leader Kim Jong-un.
- WannaCry Campaign (2017)
The spread of the WannaCry ransomware worm, which infected over 200,000 computers across 150 countries.
- Bank Heists via SWIFT (2016 – Present)
In 2016, hackers targeted the Central Bank of Bangladesh, attempting to steal $1 billion through the SWIFT system but managed to withdraw "only" $81 million.
- Cryptocurrency Theft (2018 – Present)
One of the most high-profile attacks was the 2022 hack of the Ronin Network bridge, resulting in the theft of $600 million.
Attack Methods:
- Phishing and Social Engineering (e.g., attacks through fake job offers targeting IT specialists).
- Use of Malicious Software (e.g., Remote Access Trojans – RATs).
- Exploitation of Software Vulnerabilities.
Record-Breaking Thefts and Increased Activity in 2024–2025
Hackers affiliated with North Korea stole approximately $660.5 million across 20 incidents in 2023. In 2024, this amount surged to $1.34 billion across 47 incidents—a 102.88% increase compared to the previous year. The Bybit hack alone resulted in a stolen sum that exceeded the total amount stolen by North Korea throughout 2024 by nearly $160 million.
Number of attacker addresses at the time: 4 876 (2025-02-25 12:35)
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Lazarus Group: North Korean Hacker Group


*on the graph of connections:
⚫️ - addresses that ZachXBT marked as Bybit Exploiter
Linking addresses are marked in red
2025-02-25 13:30 UTC The AML crypto team is conducting its own investigation and is also closely monitoring the publications of other blockchain specialists on the topic of Bybit Exploit. This is important, as it allows for collective cross-checking of the conclusions made.
ZachXBT on the Chainabuse portal publishes data on addresses associated with Bybit Exploit. AML crypto has drawn attention to a number of marked addresses:
TAdAXB1qNaRNnbPhF6AggZGjFDP6ndUuL8 [7 on the graph of connections]
TPgcin4u3bGY9cbHZbD3aR8ND7fHxv1Eng [49]
TRRgVeHVRa2UTSyUGEebViYq1DYGEV8uob [53]
TEiWvzw5m3avWeYZbFjoZjMPHQ8Cg39gjx [28]
TUWJqNHmcg5LWvUhMU1ngQkJFzxHMn5vbX [9]
THo4ws4A6Zhm4UukKpSChKWfR36z5Zecmg [27]
TU4Nr8bhPiMo4iNAhRPFPrkpt1vPCRofnE [41]
TUGHL3BFGFdrwWaE2eLTCSUva8DjmpwsPH [5]
TRRCnSvSK6pCwCEEiLe46A1LuyJBL4S7hZ [51]
TXL8bN4jBVrvCC1wjeRr7tPw8BYBGG9wfe [12]
While the AMLcrypto team is wondering how ZachXBT got to these addresses and if there is reason to believe they were involved in the incident, then other addresses should also be marked:
TCUkJWjhK7sK593pS6nq12P7zSykLNNj8d [13]
TA1cgLrNVWHrWGXg6H47KhpB7F51796kB7 [14]
TCyweypgUHSG8ZETwVJa1XfYw5Mh6WA9av [15]
TG5wUqBkukAho2E38ca3EZG4zvYp3hUivZ [16]
TRYLLacKZTRcyuLVRL6zS8cTNWwhmk6aHL [21]
TLmCTRMMDtgcFMxFkKVmeVZnj25EBgGL2G [22]
TMSocPC3qM1pmvahhYH7zemBf19AGGW5wp [23]
TAibbFBAkcNioexXTFWKbp65mgLp7JiqHD [24]
TJoKWUBFua3E7cM6UL1G9EJC7JkdoRmkQe [17]
TDTim4xjb2mDYnWBzgf7PpTYV4eD7cEeg2 [33]
TMzDKiuLX1q1Xnqvvim8BuQh8Gv99JbErj [34]
TEpEux1JxPn5NGVdbxzGHrcsh5H2ChKK2A [35]
TYiGFkVF7BR36rG1Nnu1BeGfL1dMh6A9ij [42]
TVmmGGnDwgmbTeemmZh4s5LoZzsavG3RfU [30]
TEtwfNRsn7kFfHotyTqpnNYaKv7sBeu7H7 [32]
TEZKYjQVENBhgi5P7CGxCdP3AfcTshFX2x [36]
TCcqJQXwkqSJNv7xZ627J8xQoS8sn42Uxp [37]
TRWjw3A3yxwBhdiz7SVvf69vZzyQNs73vw [38]
TYDpZMjeLQrv8ZCAZiWFkeMuEjzm6fdgBi [40]
TX3HCyGndvv5BhAeEdf8gymfzDgLEW7g6T [43]
TRWjLQmuWGcDC5qFMKqD5BFMJVDFTs73vw [44]
TQDEQiYewt5S14rq43vCYFaa9uNJPCtMEd [46]
TPUDEK4JSMj5JTDHZ9MzFjGmrXgHoJvvdp [48]
⚫️ - addresses that ZachXBT marked as Bybit Exploiter
Linking addresses are marked in red
2025-02-25 13:30 UTC The AML crypto team is conducting its own investigation and is also closely monitoring the publications of other blockchain specialists on the topic of Bybit Exploit. This is important, as it allows for collective cross-checking of the conclusions made.
ZachXBT on the Chainabuse portal publishes data on addresses associated with Bybit Exploit. AML crypto has drawn attention to a number of marked addresses:
TAdAXB1qNaRNnbPhF6AggZGjFDP6ndUuL8 [7 on the graph of connections]
TPgcin4u3bGY9cbHZbD3aR8ND7fHxv1Eng [49]
TRRgVeHVRa2UTSyUGEebViYq1DYGEV8uob [53]
TEiWvzw5m3avWeYZbFjoZjMPHQ8Cg39gjx [28]
TUWJqNHmcg5LWvUhMU1ngQkJFzxHMn5vbX [9]
THo4ws4A6Zhm4UukKpSChKWfR36z5Zecmg [27]
TU4Nr8bhPiMo4iNAhRPFPrkpt1vPCRofnE [41]
TUGHL3BFGFdrwWaE2eLTCSUva8DjmpwsPH [5]
TRRCnSvSK6pCwCEEiLe46A1LuyJBL4S7hZ [51]
TXL8bN4jBVrvCC1wjeRr7tPw8BYBGG9wfe [12]
While the AMLcrypto team is wondering how ZachXBT got to these addresses and if there is reason to believe they were involved in the incident, then other addresses should also be marked:
TCUkJWjhK7sK593pS6nq12P7zSykLNNj8d [13]
TA1cgLrNVWHrWGXg6H47KhpB7F51796kB7 [14]
TCyweypgUHSG8ZETwVJa1XfYw5Mh6WA9av [15]
TG5wUqBkukAho2E38ca3EZG4zvYp3hUivZ [16]
TRYLLacKZTRcyuLVRL6zS8cTNWwhmk6aHL [21]
TLmCTRMMDtgcFMxFkKVmeVZnj25EBgGL2G [22]
TMSocPC3qM1pmvahhYH7zemBf19AGGW5wp [23]
TAibbFBAkcNioexXTFWKbp65mgLp7JiqHD [24]
TJoKWUBFua3E7cM6UL1G9EJC7JkdoRmkQe [17]
TDTim4xjb2mDYnWBzgf7PpTYV4eD7cEeg2 [33]
TMzDKiuLX1q1Xnqvvim8BuQh8Gv99JbErj [34]
TEpEux1JxPn5NGVdbxzGHrcsh5H2ChKK2A [35]
TYiGFkVF7BR36rG1Nnu1BeGfL1dMh6A9ij [42]
TVmmGGnDwgmbTeemmZh4s5LoZzsavG3RfU [30]
TEtwfNRsn7kFfHotyTqpnNYaKv7sBeu7H7 [32]
TEZKYjQVENBhgi5P7CGxCdP3AfcTshFX2x [36]
TCcqJQXwkqSJNv7xZ627J8xQoS8sn42Uxp [37]
TRWjw3A3yxwBhdiz7SVvf69vZzyQNs73vw [38]
TYDpZMjeLQrv8ZCAZiWFkeMuEjzm6fdgBi [40]
TX3HCyGndvv5BhAeEdf8gymfzDgLEW7g6T [43]
TRWjLQmuWGcDC5qFMKqD5BFMJVDFTs73vw [44]
TQDEQiYewt5S14rq43vCYFaa9uNJPCtMEd [46]
TPUDEK4JSMj5JTDHZ9MzFjGmrXgHoJvvdp [48]
*on the graph of connections:
⚫️ - addresses that ZachXBT marked as Bybit Exploiter
Linking addresses are marked in red
2025-02-25 13:30 UTC The AML crypto team is conducting its own investigation and is also closely monitoring the publications of other blockchain specialists on the topic of Bybit Exploit. This is important, as it allows for collective cross-checking of the conclusions made.
ZachXBT on the Chainabuse portal publishes data on addresses associated with Bybit Exploit. AML crypto has drawn attention to a number of marked addresses:
While the AMLcrypto team is wondering how ZachXBT got to these addresses and if there is reason to believe they were involved in the incident, then other addresses should also be marked:
⚫️ - addresses that ZachXBT marked as Bybit Exploiter
Linking addresses are marked in red
2025-02-25 13:30 UTC The AML crypto team is conducting its own investigation and is also closely monitoring the publications of other blockchain specialists on the topic of Bybit Exploit. This is important, as it allows for collective cross-checking of the conclusions made.
ZachXBT on the Chainabuse portal publishes data on addresses associated with Bybit Exploit. AML crypto has drawn attention to a number of marked addresses:
- TAdAXB1qNaRNnbPhF6AggZGjFDP6
- TPgcin4u3bGY9cbHZbD3aR8ND7fHx
- TRRgVeHVRa2UTSyUGEebViYq1DYG
- TEiWvzw5m3avWeYZbFjoZjMPHQ8C
- TUWJqNHmcg5LWvUhMU1ngQkJFz
- THo4ws4A6Zhm4UukKpSChKWfR36
- TU4Nr8bhPiMo4iNAhRPFPrkpt1vPC
- TUGHL3BFGFdrwWaE2eLTCSUva8Dj
- TRRCnSvSK6pCwCEEiLe46A1LuyJBL
- TXL8bN4jBVrvCC1wjeRr7tPw8BYBG
While the AMLcrypto team is wondering how ZachXBT got to these addresses and if there is reason to believe they were involved in the incident, then other addresses should also be marked:
- TCUkJWjhK7sK593pS6nq12P7zSykL
- TA1cgLrNVWHrWGXg6H47KhpB7F5
- TCyweypgUHSG8ZETwVJa1XfYw5M
- TG5wUqBkukAho2E38ca3EZG4zvYp
- TRYLLacKZTRcyuLVRL6zS8cTNWwh
- TLmCTRMMDtgcFMxFkKVmeVZnj25
- TMSocPC3qM1pmvahhYH7zemBf19
- TAibbFBAkcNioexXTFWKbp65mgLp7
- TJoKWUBFua3E7cM6UL1G9EJC7Jk
- TDTim4xjb2mDYnWBzgf7PpTYV4eD
- TMzDKiuLX1q1Xnqvvim8BuQh8Gv99
- TEpEux1JxPn5NGVdbxzGHrcsh5H2
- TYiGFkVF7BR36rG1Nnu1BeGfL1dM
- TVmmGGnDwgmbTeemmZh4s5LoZ
- TEtwfNRsn7kFfHotyTqpnNYaKv7sBe
- TEZKYjQVENBhgi5P7CGxCdP3AfcTs
- TCcqJQXwkqSJNv7xZ627J8xQoS8s
- TRWjw3A3yxwBhdiz7SVvf69vZzyQN
- TYDpZMjeLQrv8ZCAZiWFkeMuEjzm
- TX3HCyGndvv5BhAeEdf8gymfzDgLE
- TRWjLQmuWGcDC5qFMKqD5BFMJ
- TQDEQiYewt5S14rq43vCYFaa9uNJP
- TPUDEK4JSMj5JTDHZ9MzFjGmrXg
Data Verification “The Key to Success”


Transaction hash: 0x0a1c34806d862ad82936a38ce24c406120e236cf036e06e2e72a835e348aa233
Bybit exploiter address: 0x81eFb9709D403493DCdCA0f1e27aD4D82A4168a5
Gate IO deposit address: 0x60b30037aD28b63BBbC29155c4eC876E472EeC86
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Bybit exploiter address: 0x81eFb9709D403493DCdCA0f1e27aD4D82A4168a5
Gate IO deposit address: 0x60b30037aD28b63BBbC29155c4eC876E472EeC86
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Transaction hash: 0x0a1c34806d862ad82936a38ce24c406
120e236cf036e06e2e72a835e348aa233
Bybit exploiter address: 0x81eFb9709D403493DCdCA0f1e27aD
4D82A4168a5
Gate IO deposit address: 0x60b30037aD28b63BBbC29155c4eC8
76E472EeC86
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
120e236cf036e06e2e72a835e348aa233
Bybit exploiter address: 0x81eFb9709D403493DCdCA0f1e27aD
4D82A4168a5
Gate IO deposit address: 0x60b30037aD28b63BBbC29155c4eC8
76E472EeC86
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
2025-02-25 3:22:11 a portion of the stolen funds in the amount of 1.1242264 ETH was deposited to the Gate IO exchange deposit address.

*Legend on the transaction graph:
[1] - Bybit exploiter addresses cluster
[2,3,4,5,6,7,8,9] - Bybit exploiter addresses
[10,11,12,13,14,15,16] - HitBTC deposit addresses
Transaction hashes:
0x3de4657b5b721c4e166b0c75d07b30fc65758f0f51d763f4182fece364f2934f
0x8e6c12fa61d13c779633d1abb41b1f37d30181e5c990cd57a64c800a240e7104
0x405be08d91be46d46df0ef15343b57c5f20116b68ee3a7eedbd2743c8b9b556a
0xfac437e6796cef79d596dd3233866788d38239ff951475269162322c67031e07
0xa978b8b8407f437fc389e00ce6496357e872456d6a2839d2ec2ad8c48e1d55a9
0x397bec85ebbccfc6387686a6d0ac0e1134a66867046f16e84aa3fd3bca6c508c
0x2015a55d31ec6d7a086e330536daaeef8c93137f950869499890f8bccef44ed4
Bybit addresses exploiter:
0x2340b61caf2df1d61b0e9b42235f712bbe04c782 [3]
0xa6937bf41ee94dc6fab7d57577a9e9feab0101c1 [4]
0x286b425f3cf99b24e075043739f7faa9ca0ac2b6 [5]
0xeab7d41f583863984d2d4a0a8bf56f7006f93c43 [6]
0x43115427da5d02c7cb0d677056e369bb032fd8d2 [7]
0x8d1dca7d5187b1fa5571c11944bc71eb1979d115 [8]
0x44c9f73c3afd708d406db7557535ad852b262602 [9]
Deposit addresses HitBTC:
0x3cA9EEF657bA441DF9b05Da5C54cf4053057f40a [10]
0x0cBf954D0176BC12445460D355eF383c4B6effaD [11]
0x151534FC47fDc4FEdAd9B125D96b3E0D7D608C2b [12]
0xeA7b46cD64F2990aFA82ab90ee7b3860Cd72f97a [13]
0xB92158f660129596C473d792B2F0eB2Fee3E7E0d [14]
0x5f05d30eA26c290B092773cB00052A806390Aab9 [15]
0x71D76Dd389C3763D50b4928232E017CEDfedc39b [16]
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
[1] - Bybit exploiter addresses cluster
[2,3,4,5,6,7,8,9] - Bybit exploiter addresses
[10,11,12,13,14,15,16] - HitBTC deposit addresses
Transaction hashes:
0x3de4657b5b721c4e166b0c75d07b30fc65758f0f51d763f4182fece364f2934f
0x8e6c12fa61d13c779633d1abb41b1f37d30181e5c990cd57a64c800a240e7104
0x405be08d91be46d46df0ef15343b57c5f20116b68ee3a7eedbd2743c8b9b556a
0xfac437e6796cef79d596dd3233866788d38239ff951475269162322c67031e07
0xa978b8b8407f437fc389e00ce6496357e872456d6a2839d2ec2ad8c48e1d55a9
0x397bec85ebbccfc6387686a6d0ac0e1134a66867046f16e84aa3fd3bca6c508c
0x2015a55d31ec6d7a086e330536daaeef8c93137f950869499890f8bccef44ed4
Bybit addresses exploiter:
0x2340b61caf2df1d61b0e9b42235f712bbe04c782 [3]
0xa6937bf41ee94dc6fab7d57577a9e9feab0101c1 [4]
0x286b425f3cf99b24e075043739f7faa9ca0ac2b6 [5]
0xeab7d41f583863984d2d4a0a8bf56f7006f93c43 [6]
0x43115427da5d02c7cb0d677056e369bb032fd8d2 [7]
0x8d1dca7d5187b1fa5571c11944bc71eb1979d115 [8]
0x44c9f73c3afd708d406db7557535ad852b262602 [9]
Deposit addresses HitBTC:
0x3cA9EEF657bA441DF9b05Da5C54cf4053057f40a [10]
0x0cBf954D0176BC12445460D355eF383c4B6effaD [11]
0x151534FC47fDc4FEdAd9B125D96b3E0D7D608C2b [12]
0xeA7b46cD64F2990aFA82ab90ee7b3860Cd72f97a [13]
0xB92158f660129596C473d792B2F0eB2Fee3E7E0d [14]
0x5f05d30eA26c290B092773cB00052A806390Aab9 [15]
0x71D76Dd389C3763D50b4928232E017CEDfedc39b [16]
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
*Legend on the transaction graph:
[1] - Bybit exploiter addresses cluster
[2,3,4,5,6,7,8,9] - Bybit exploiter addresses
[10,11,12,13,14,15,16] - HitBTC deposit addresses
Transaction hashes:
104
56a
1e07
55a9
08c
d4
Bybit addresses exploiter:
Deposit addresses HitBTC:
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
[1] - Bybit exploiter addresses cluster
[2,3,4,5,6,7,8,9] - Bybit exploiter addresses
[10,11,12,13,14,15,16] - HitBTC deposit addresses
Transaction hashes:
- 0x3de4657b5b721c4e166b0c75d07b
- 0x8e6c12fa61d13c779633d1abb41b1
104
- 0x405be08d91be46d46df0ef15343b
56a
- 0xfac437e6796cef79d596dd323386
1e07
- 0xa978b8b8407f437fc389e00ce649
55a9
- 0x397bec85ebbccfc6387686a6d0ac
08c
- 0x2015a55d31ec6d7a086e330536da
d4
Bybit addresses exploiter:
- 0x2340b61caf2df1d61b0e9b42235f7
- 0xa6937bf41ee94dc6fab7d57577a9
- 0x286b425f3cf99b24e075043739f7f
- 0xeab7d41f583863984d2d4a0a8bf5
- 0x43115427da5d02c7cb0d677056e3
- 0x8d1dca7d5187b1fa5571c11944bc
- 0x44c9f73c3afd708d406db7557535
Deposit addresses HitBTC:
- 0x3cA9EEF657bA441DF9b05Da5C5
- 0x0cBf954D0176BC12445460D355e
- 0x151534FC47fDc4FEdAd9B125D96
- 0xeA7b46cD64F2990aFA82ab90ee7
- 0xB92158f660129596C473d792B2F
- 0x5f05d30eA26c290B092773cB000
- 0x71D76Dd389C3763D50b4928232
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
2025-02-25 from 5:14:11 to 5:51:59, part of the funds stolen during the Bybit exploit in the total amount of 17.84984 ETH was transferred in seven transactions to the deposit address of the HitBTC exchange.

Ben Zhou announced the launch of lazarusbounty.com, a website that provides full transparency into Lazarus money laundering. The platform allows you to connect your wallet, help track funds, and receive an instant reward if your data leads to the freezing of funds. The entire chain of participants, including exchanges and mixers, receives a share of the reward. The site also provides a rating of honest and dishonest participants, which motivates companies to avoid being blacklisted.
More features are planned for the future, such as real-time wallet balance updates, tools for regulators, and expanded support for other Lazarus victims.
Number of attacker addresses at the time: 6 469
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
More features are planned for the future, such as real-time wallet balance updates, tools for regulators, and expanded support for other Lazarus victims.
Number of attacker addresses at the time: 6 469
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Ben Zhou declares hunting season on Lazarus Hacker group
AML Crypto team has identified the flow of ETH from address 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2 through the Solana and Binance Smart Chain networks into Bitcoin. The conversion was carried out using the Debridge and Bridgers bridges.
Number of attacker addresses at the time: 6 527
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Number of attacker addresses at the time: 6 527
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
AML Crypto team has identified the flow of ETH from address 0x47666Fab8bd0Ac7003bce3f
5C3585383F09486E2 through the Solana and Binance Smart Chain networks into Bitcoin. The conversion was carried out using the Debridge and Bridgers bridges.
Number of attacker addresses at the time: 6 527
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
5C3585383F09486E2 through the Solana and Binance Smart Chain networks into Bitcoin. The conversion was carried out using the Debridge and Bridgers bridges.
Number of attacker addresses at the time: 6 527
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

Elliptic launches free data feed on illegal addresses linked to Bybit exploit
Number of attacker addresses at the time: 6 527
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Number of attacker addresses at the time: 6 527
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Bybit Hack Details via Elliptic API
DAY 6. 2025-02-26
AML Crypto conducted an express analysis of information from the API presented the day before by Elliptic, and identified a number of addresses that should be re-checked for involvement in the incident.
According to AML Crypto, a number of addresses belong to users, as well as various services.
AML Crypto also shared its API with data on Bybit Exploit for joint data verification and markup refinement.
Number of attacker addresses at the time: 6 527
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
According to AML Crypto, a number of addresses belong to users, as well as various services.
AML Crypto also shared its API with data on Bybit Exploit for joint data verification and markup refinement.
Number of attacker addresses at the time: 6 527
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

AML Crypto Calls on Elliptic to Collaborate on Bybit Exploit Data Sharing
Transaction hash: 0x31564b2cb2cb4ec253e1dc3fd9f905ea315973b3bc02cb08b6f3caba240084e6
Bybit exploiter address [6]: 0x69a2c4e62ae16eaa17c9639844e7640a4ee59474
n-exchange deposit address [7]: 0x1bac08001d761c303901d5e32273a24c07d3f3da
*Graph of connections:
[1,2,3,4,5,6] - Bybit exploiter addresses
[7] - N-exchange address
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Bybit exploiter address [6]: 0x69a2c4e62ae16eaa17c9639844e7640a4ee59474
n-exchange deposit address [7]: 0x1bac08001d761c303901d5e32273a24c07d3f3da
*Graph of connections:
[1,2,3,4,5,6] - Bybit exploiter addresses
[7] - N-exchange address
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Transaction hash: 0x31564b2cb2cb4ec
253e1dc3fd9f905ea315973b3bc02cb08
b6f3caba240084e6
Bybit exploiter address [6]: 0x69a2c4e62
ae16eaa17c9639844e7640a4ee59474
n-exchange deposit address [7]: 0x1bac0
8001d761c303901d5e32273a24c07d3f
3da
*Graph of connections:
[1,2,3,4,5,6] - Bybit exploiter addresses
[7] - N-exchange address
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
253e1dc3fd9f905ea315973b3bc02cb08
b6f3caba240084e6
Bybit exploiter address [6]: 0x69a2c4e62
ae16eaa17c9639844e7640a4ee59474
n-exchange deposit address [7]: 0x1bac0
8001d761c303901d5e32273a24c07d3f
3da
*Graph of connections:
[1,2,3,4,5,6] - Bybit exploiter addresses
[7] - N-exchange address
API for getting blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

2025-02-25 at 11:18:23 (UTC) part of the stolen funds during the Bybit exploit in the amount of 56.19212221 ETH was sent to the address of the n-exchange exchanger.
The number of transactions and blockchain addresses of the attackers is in the thousands. Perception of this data even in the form of a graph becomes problematic. The AML Crypto team decided to demonstrate a simplified graph with data on the Ethereum network, where intermediate addresses are combined into clusters. The main focus is on known counterparties with whom the attackers interacted.
The graph shows how funds are distributed and partially withdrawn through various centralized and decentralized services that could be used for laundering and cashing out.
Key Takeaways:
1. Starting Point– Bybit Cold Wallet.
2. Flow of Funds – Funds were distributed across multiple linked addresses before arriving at the services involved in the incident.
3. Final Destinations – Funds arrived at centralized exchanges and services, decentralized bridges, protocols and exchangers, and storage addresses.
Centralized services that received funds:
- eXch.cx
- ChangeNOW
- n.exchange
- Gate.io
- HitBTC
Decentralized services:
- OKX Web3
- Uniswap
- LiFi
- Maya Protocol
- Thorchain
- Across Protocol
- Mimic.fi
- 1inch Network
- Bridgers
- Transit Finance
- Symbiosis Finance
- ParaSwap
Number of attacker addresses at the time: 7 024
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
The graph shows how funds are distributed and partially withdrawn through various centralized and decentralized services that could be used for laundering and cashing out.
Key Takeaways:
1. Starting Point– Bybit Cold Wallet.
2. Flow of Funds – Funds were distributed across multiple linked addresses before arriving at the services involved in the incident.
3. Final Destinations – Funds arrived at centralized exchanges and services, decentralized bridges, protocols and exchangers, and storage addresses.
Centralized services that received funds:
- eXch.cx
- ChangeNOW
- n.exchange
- Gate.io
- HitBTC
Decentralized services:
- OKX Web3
- Uniswap
- LiFi
- Maya Protocol
- Thorchain
- Across Protocol
- Mimic.fi
- 1inch Network
- Bridgers
- Transit Finance
- Symbiosis Finance
- ParaSwap
Number of attacker addresses at the time: 7 024
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

AML Crypto presents simplified and visual transaction graph of attackers
The forensics investigation of the three signers’ hosts suggests the root cause of the attack is malicious code originating from
Safe{Wallet}’s infrastructure.
No indication of compromise was identified within
Bybit’s infrastructure.
The investigation is still ongoing to further confirm the findings.
Preliminary Conclusions
- The benign JavaScript file of app.safe.global appears to have been replaced with malicious code on February 19, 2025, at 15:29:25 UTC, specifically targeting Ethereum Multisig Cold Wallet of Bybit (0x1Db92e2EeBC8E0c075a02BeA49a2935BcD2dFCF4). The attack was designed to activate during the next Bybit transaction, which occurred on February 21, 2025, at 14:13:35 UTC.
- Based on the investigation results from the machines of Bybit’s Signers and the cached malicious JavaScript payload found on the Wayback Archive, we strongly conclude that AWS S3 or CloudFront account/API Key of Safe.Global was likely leaked or compromised.
*(Note: In September 2024, Google Search announced its integration with the Wayback Archive, providing direct links to cached website versions on the Wayback Machine. This validates the legitimacy of the cached malicious file.)*
- Further investigation should be conducted to validate the findings and the root cause.
Number of attacker addresses at the time: 7 024
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Safe{Wallet}’s infrastructure.
No indication of compromise was identified within
Bybit’s infrastructure.
The investigation is still ongoing to further confirm the findings.
Preliminary Conclusions
- The benign JavaScript file of app.safe.global appears to have been replaced with malicious code on February 19, 2025, at 15:29:25 UTC, specifically targeting Ethereum Multisig Cold Wallet of Bybit (0x1Db92e2EeBC8E0c075a02BeA49a2935BcD2dFCF4). The attack was designed to activate during the next Bybit transaction, which occurred on February 21, 2025, at 14:13:35 UTC.
- Based on the investigation results from the machines of Bybit’s Signers and the cached malicious JavaScript payload found on the Wayback Archive, we strongly conclude that AWS S3 or CloudFront account/API Key of Safe.Global was likely leaked or compromised.
*(Note: In September 2024, Google Search announced its integration with the Wayback Archive, providing direct links to cached website versions on the Wayback Machine. This validates the legitimacy of the cached malicious file.)*
- Further investigation should be conducted to validate the findings and the root cause.
Number of attacker addresses at the time: 7 024
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
The forensics investigation of the three signers’ hosts suggests the root cause of the attack is malicious code originating from
Safe{Wallet}’s infrastructure.
No indication of compromise was identified within
Bybit’s infrastructure.
The investigation is still ongoing to further confirm the findings.
Preliminary Conclusions
- The benign JavaScript file of app.safe.global appears to have been replaced with malicious code on February 19, 2025, at 15:29:25 UTC, specifically targeting Ethereum Multisig Cold Wallet of Bybit (0x1Db92e2EeBC8E0c075a02BeA49a2
935BcD2dFCF4). The attack was designed to activate during the next Bybit transaction, which occurred on February 21, 2025, at 14:13:35 UTC.
- Based on the investigation results from the machines of Bybit’s Signers and the cached malicious JavaScript payload found on the Wayback Archive, we strongly conclude that AWS S3 or CloudFront account/API Key of Safe.Global was likely leaked or compromised.
*(Note: In September 2024, Google Search announced its integration with the Wayback Archive, providing direct links to cached website versions on the Wayback Machine. This validates the legitimacy of the cached malicious file.)*
- Further investigation should be conducted to validate the findings and the root cause.
Number of attacker addresses at the time: 7 024
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Safe{Wallet}’s infrastructure.
No indication of compromise was identified within
Bybit’s infrastructure.
The investigation is still ongoing to further confirm the findings.
Preliminary Conclusions
- The benign JavaScript file of app.safe.global appears to have been replaced with malicious code on February 19, 2025, at 15:29:25 UTC, specifically targeting Ethereum Multisig Cold Wallet of Bybit (0x1Db92e2EeBC8E0c075a02BeA49a2
935BcD2dFCF4). The attack was designed to activate during the next Bybit transaction, which occurred on February 21, 2025, at 14:13:35 UTC.
- Based on the investigation results from the machines of Bybit’s Signers and the cached malicious JavaScript payload found on the Wayback Archive, we strongly conclude that AWS S3 or CloudFront account/API Key of Safe.Global was likely leaked or compromised.
*(Note: In September 2024, Google Search announced its integration with the Wayback Archive, providing direct links to cached website versions on the Wayback Machine. This validates the legitimacy of the cached malicious file.)*
- Further investigation should be conducted to validate the findings and the root cause.
Number of attacker addresses at the time: 7 024
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist



2025-02-25 15:17 UTC Ben Zhou [provided] preliminary data from the hack report in his post**==
The interview not only detailed the steps taken to manage the crisis but also revealed the personal toll the incident has taken on Zhou, who confessed that the past few days have been some of the most stressful of his life.
Immediate Reaction and Crisis Management
Questions:
- What was your immediate reaction to the news of the hack?
- How have you been handling the stress and managing the situation?
Answers:
- Zhou emphasized that his first reaction was to mitigate the damage and keep the company's operations open to maintain client trust. He deliberately avoided halting withdrawals to prevent panic among users.
- In managing stress, Zhou noted that personal circumstances cause him more stress than professional ones, highlighting his commitment to maintaining balance and resilience during crisis periods.
Financial Stability and Transparency
Questions:
- How does ByBit plan to cover the financial losses?
- What steps have you taken to ensure transparency towards your clients and the public?
Answers:
- Zhou assured that ByBit has sufficient funds to cover the losses, underscoring the company's financial stability.
- He has actively engaged with the public through social media and other communication channels, demonstrating openness and transparency in crisis management.
Enhancing Technical Security
Questions:
- What lessons has ByBit learned from this hack in terms of security?
- What technical changes are planned to prevent future hacks?
Answers:
- Zhou confirmed that the company will strengthen security measures, including the development of proprietary solutions for managing cryptocurrency wallets.
- Plans are in place to enhance security systems and infrastructure to ensure a higher level of asset protection for clients.
Personal Reflections and Future Outlook
Questions:
- What personal lessons and insights have you gained from this experience?
- How does this impact your vision for the future of cryptocurrencies and ByBit?
Answers:
- Zhou spoke about the importance of managing a crisis with professionalism and dignity, aiming to use this experience to improve corporate standards and practices.
- He expressed confidence that such challenges strengthen the industry and contribute to the development of more secure and robust technologies.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Immediate Reaction and Crisis Management
Questions:
- What was your immediate reaction to the news of the hack?
- How have you been handling the stress and managing the situation?
Answers:
- Zhou emphasized that his first reaction was to mitigate the damage and keep the company's operations open to maintain client trust. He deliberately avoided halting withdrawals to prevent panic among users.
- In managing stress, Zhou noted that personal circumstances cause him more stress than professional ones, highlighting his commitment to maintaining balance and resilience during crisis periods.
Financial Stability and Transparency
Questions:
- How does ByBit plan to cover the financial losses?
- What steps have you taken to ensure transparency towards your clients and the public?
Answers:
- Zhou assured that ByBit has sufficient funds to cover the losses, underscoring the company's financial stability.
- He has actively engaged with the public through social media and other communication channels, demonstrating openness and transparency in crisis management.
Enhancing Technical Security
Questions:
- What lessons has ByBit learned from this hack in terms of security?
- What technical changes are planned to prevent future hacks?
Answers:
- Zhou confirmed that the company will strengthen security measures, including the development of proprietary solutions for managing cryptocurrency wallets.
- Plans are in place to enhance security systems and infrastructure to ensure a higher level of asset protection for clients.
Personal Reflections and Future Outlook
Questions:
- What personal lessons and insights have you gained from this experience?
- How does this impact your vision for the future of cryptocurrencies and ByBit?
Answers:
- Zhou spoke about the importance of managing a crisis with professionalism and dignity, aiming to use this experience to improve corporate standards and practices.
- He expressed confidence that such challenges strengthen the industry and contribute to the development of more secure and robust technologies.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Ben Zhou, CEO of ByBit, opened up about his response to the massive $1.4 billion hack in a recent interview on the MR SHIFT podcast.
Now, in real-time, you can track ByBit’s data on the flow of stolen funds across crypto addresses, spanning multiple blockchain networks.
This service from ByBit not only provides valuable insights into the ongoing investigation but also offers rewards for helping block the stolen funds. Anyone can contribute to solving the case and earn a reward for their assistance.
Additionally, the platform features a list of “bounty hunters” who have already received their rewards. To date, 12 participants have been paid $4,226,778 for their active involvement in the investigation.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
This service from ByBit not only provides valuable insights into the ongoing investigation but also offers rewards for helping block the stolen funds. Anyone can contribute to solving the case and earn a reward for their assistance.
Additionally, the platform features a list of “bounty hunters” who have already received their rewards. To date, 12 participants have been paid $4,226,778 for their active involvement in the investigation.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

Updates on the Lazarus Bounty platform: a new interactive graph has been added to the website, displaying data related to money laundering from the ByBit hack.
In the released statement, U.S. authorities clarified that the hackers used specialized software called TraderTraitor. This malicious tool disguises itself as legitimate cryptocurrency trading programs but is built on open-source code. The software was written in JavaScript using Node.js and the Electron framework, as reported in the FBI bulletin from April 18, 2022.
According to the FBI, the TraderTraitor tool is used by a hacking group sponsored by the North Korean government, known as Lazarus Group, APT38, BlueNoroff, and Stardust Chollima. Their activities have been tracked since 2020.
“Participants of TraderTraitor act swiftly, having already converted part of the stolen assets into Bitcoin and other virtual assets, distributed across thousands of addresses on multiple blockchains. These assets are expected to be laundered and eventually converted into fiat currency,”
the FBI statement says.
The FBI also published the addresses of the stolen Ethereum and urged to block any transactions associated with these addresses.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
According to the FBI, the TraderTraitor tool is used by a hacking group sponsored by the North Korean government, known as Lazarus Group, APT38, BlueNoroff, and Stardust Chollima. Their activities have been tracked since 2020.
“Participants of TraderTraitor act swiftly, having already converted part of the stolen assets into Bitcoin and other virtual assets, distributed across thousands of addresses on multiple blockchains. These assets are expected to be laundered and eventually converted into fiat currency,”
the FBI statement says.
The FBI also published the addresses of the stolen Ethereum and urged to block any transactions associated with these addresses.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
FBI in official statement attributes the $1.5B Ethereum theft from Bybit to North Korean hackers
The main focus is on how the front-end code of the Safe wallet was compromised, highlighting the critical importance of strict code control in cryptocurrency projects.
The full versions of the attack reports are available here.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
The full versions of the attack reports are available here.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

SlowMist, in collaboration with Safe, has released an official report on how hackers exploited vulnerabilities in development environments and supply chains to carry out the $1.5 billion theft from the Bybit exchange and Safe wallets.
FBI Confirmation: The U.S. Federal Bureau of Investigation has officially stated that North Korea is responsible for the Bybit hack, which resulted in the theft of approximately $1.5 billion in cryptocurrency (mostly Ethereum). The FBI links the attack to the Lazarus Group, a hacking group known for its cybercrimes.
Bybit Initiative: Bybit CEO Ben Zhou announced a $140 million reward program aimed at encouraging the crypto community to help track and freeze the stolen assets. On Bybit’s dedicated website, progress has already been reported: part of the funds have been frozen, and some exchanges and participants have been rewarded for their assistance.
Investigation and Findings: Forensic analysis revealed that the hack did not occur due to vulnerabilities in Bybit’s systems, but rather through the compromise of Safe{Wallet} infrastructure, which Bybit uses for multi-signature wallets. Hackers injected malicious code into Safe's servers, enabling them to redirect funds during a scheduled transfer from cold storage to hot wallets.
Market Reaction: The hack has led to panic-driven withdrawals from cryptocurrency exchanges, totaling more than $4.3 billion, and has exacerbated the exodus of stakers from centralized platforms like Bybit. This is seen as a blow to confidence in institutional staking.
Movement of Funds: The hackers have already laundered around $335 million of the stolen assets (approximately one-third of the total amount) using decentralized exchanges and cross-chain bridges. The remaining funds (about $900 million) are still on addresses controlled by the perpetrators.
Regulatory Actions: The FBI has urged crypto node operators and exchanges to block transactions associated with the hackers' addresses to prevent further money laundering.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Bybit Initiative: Bybit CEO Ben Zhou announced a $140 million reward program aimed at encouraging the crypto community to help track and freeze the stolen assets. On Bybit’s dedicated website, progress has already been reported: part of the funds have been frozen, and some exchanges and participants have been rewarded for their assistance.
Investigation and Findings: Forensic analysis revealed that the hack did not occur due to vulnerabilities in Bybit’s systems, but rather through the compromise of Safe{Wallet} infrastructure, which Bybit uses for multi-signature wallets. Hackers injected malicious code into Safe's servers, enabling them to redirect funds during a scheduled transfer from cold storage to hot wallets.
Market Reaction: The hack has led to panic-driven withdrawals from cryptocurrency exchanges, totaling more than $4.3 billion, and has exacerbated the exodus of stakers from centralized platforms like Bybit. This is seen as a blow to confidence in institutional staking.
Movement of Funds: The hackers have already laundered around $335 million of the stolen assets (approximately one-third of the total amount) using decentralized exchanges and cross-chain bridges. The remaining funds (about $900 million) are still on addresses controlled by the perpetrators.
Regulatory Actions: The FBI has urged crypto node operators and exchanges to block transactions associated with the hackers' addresses to prevent further money laundering.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Today, February 27, 2025, the Bybit exchange hack, which occurred on February 21 and became the largest cryptocurrency heist in history, continues to dominate the news. Here are the key events and updates currently being reported:
According to Arkham ETH totaling 240 million was mostly exchanged for native BTC.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist




Arkham analytics platform claims that the Lazarus group laundered $240 million of stolen funds through Thorchain.
Ben Zhou, CEO of Bybit, has published a new post about an important update to the Lazarus Bounty platform, which now provides more detailed information and enhanced features for bounty hunters involved in the investigation of the Bybit theft. Here are the main updates:
1. Hacker Address Analysis: The platform now allows users to view all assets spread across various blockchains. This will enable bounty hunters to get a complete picture of the stolen funds and track them more accurately.
2. Creation of a Discord Channel: An official Discord channel has been created for bounty hunters, where they can submit their reports and receive automatic notifications if their found addresses have already been flagged by other participants.
3. Hacker Wallet Balances: Wallet balances of the hackers are now displayed on the platform, ranked by the amount in each wallet. This simplifies the process of tracking and blocking the stolen funds.
4. Verified Reports: Reports will now display the bounty hunter’s name, adding transparency and recognizing the efforts of the participants.
Summary: Since the launch of the website, 2,167 reports have been processed. All reports have been reviewed, and the platform continues to operate with high efficiency.
Ben Zhou also mentioned that more updates and improvements are expected to come soon.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
1. Hacker Address Analysis: The platform now allows users to view all assets spread across various blockchains. This will enable bounty hunters to get a complete picture of the stolen funds and track them more accurately.
2. Creation of a Discord Channel: An official Discord channel has been created for bounty hunters, where they can submit their reports and receive automatic notifications if their found addresses have already been flagged by other participants.
3. Hacker Wallet Balances: Wallet balances of the hackers are now displayed on the platform, ranked by the amount in each wallet. This simplifies the process of tracking and blocking the stolen funds.
4. Verified Reports: Reports will now display the bounty hunter’s name, adding transparency and recognizing the efforts of the participants.
Summary: Since the launch of the website, 2,167 reports have been processed. All reports have been reviewed, and the platform continues to operate with high efficiency.
Ben Zhou also mentioned that more updates and improvements are expected to come soon.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

Updates from Bybit CEO Ben Zhou on Lazarus Bounty: Key Changes and New Features
On 2025-02-28 at 7:45 PM, renowned investigator ZachXBT noted in his response to Circle CEO's tweet that Tether Limited blocked $106k USDT on crypto addresses involved in the ByBit hack, and Circle in turn $115k USDC within 5 hours, even though they could have done so.
"How many more examples will people have to show until the space understands Circle is a bad actor." - ZachXBT summarizes
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
"How many more examples will people have to show until the space understands Circle is a bad actor." - ZachXBT summarizes
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

ZachXBT: Tether froze $106k and Circle is a "bad actor".
Thorchain is a decentralized cross-chain platform enabling direct cryptocurrency swaps between different blockchains without intermediaries (DEX). Instead of relying on centralized exchanges, Thorchain claims to use its proprietary protocol for secure and efficient asset exchanges.
🌐 How does it work?
Thorchain allows users to swap assets like Bitcoin, Ethereum, BNB, and others without centralized exchanges. Instead, it uses RUNE* — the native token that ensures liquidity.
*RUNE in Thorchain acts as the mediator in every swap, linking assets in liquidity pools. The token also secures the network through node operator obligations and participates in governance. Users don’t need to hold RUNE — swaps occur automatically via pools.
💡 Key Facts:
- Founded in 2018, mainnet launched in 2022. In 2021, it suffered a $7.6 million hack — losses were fully compensated.
- After the ByBit hack in February 2025, the volume of exchanges increased several times.
- January 25, 2025: Paused BTC and ETH lending due to debt to prevent insolvency and restructure protocol liabilities.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
🌐 How does it work?
Thorchain allows users to swap assets like Bitcoin, Ethereum, BNB, and others without centralized exchanges. Instead, it uses RUNE* — the native token that ensures liquidity.
*RUNE in Thorchain acts as the mediator in every swap, linking assets in liquidity pools. The token also secures the network through node operator obligations and participates in governance. Users don’t need to hold RUNE — swaps occur automatically via pools.
💡 Key Facts:
- Founded in 2018, mainnet launched in 2022. In 2021, it suffered a $7.6 million hack — losses were fully compensated.
- After the ByBit hack in February 2025, the volume of exchanges increased several times.
- January 25, 2025: Paused BTC and ETH lending due to debt to prevent insolvency and restructure protocol liabilities.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
What is Thorchain?
According to Bitrace monitoring data, as of March 2, 2025, Tether and Circle have blocked these addresses on Ethereum and Tron that have been linked to the hacker. This action successfully intercepted over 760,000 USDT and USDC.
Addresses specified by Bitrace:
0xDa2e12E94060720581994eEc870F83d9C7200c2c
TUMYJzs4A9vyd2SuGjtUPdRiJc3nnZpqvQ
TAJmG7UbrqAspo6eGh2oKD3xYr6kZSi9QS
THYi1FE1rbUoqsKfft9C2wSznhh53HbRKN
TEa1NpRPax9KiRXF2WBhcPfU4B8jt8zUiQ
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Addresses specified by Bitrace:
0xDa2e12E94060720581994eEc870F83d9C7200c2c
TUMYJzs4A9vyd2SuGjtUPdRiJc3nnZpqvQ
TAJmG7UbrqAspo6eGh2oKD3xYr6kZSi9QS
THYi1FE1rbUoqsKfft9C2wSznhh53HbRKN
TEa1NpRPax9KiRXF2WBhcPfU4B8jt8zUiQ
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
According to Bitrace monitoring data, as of March 2, 2025, Tether and Circle have blocked these addresses on Ethereum and Tron that have been linked to the hacker. This action successfully intercepted over 760,000 USDT and USDC.
Addresses specified by Bitrace:
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Addresses specified by Bitrace:
- 0xDa2e12E94060720581994eEc87
- TUMYJzs4A9vyd2SuGjtUPdRiJc3n
- TAJmG7UbrqAspo6eGh2oKD3xYr6k
- THYi1FE1rbUoqsKfft9C2wSznhh53
- TEa1NpRPax9KiRXF2WBhcPfU4B8j
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

Tether and Circle have frozen at least five addresses linked to hackers who stole funds from the exchange, intercepting a total of $760,000.
THORChain recorded a record increase in activity following the major $14 billion hack of cryptocurrency exchange Bybit. Trading volume for March 2 exceeded $1 billion, several times more than any other day in 2025 before the ByBit hack.
Recall that on February 28, the Arkham analytics platform claimed that the Lazarus group was laundering $240 million of stolen funds through Thorchain.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Recall that on February 28, the Arkham analytics platform claimed that the Lazarus group was laundering $240 million of stolen funds through Thorchain.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

THORChain's daily trading volume exceeded $1 billion after the Bybit hack
Ben Zhou, CEO of Bybit, shared important information on the progress of the $1.4 billion theft investigation, including over 500,000 ETH stolen from the platform. According to him, the current status is as follows:
Key points:
Bounty Program Updates:
Full details are available on LazarusBounty.com.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
- 77% of the stolen funds are traceable.
- 20% of the funds have gone dark and are no longer traceable.
- 3% of the funds have been frozen.
Key points:
- 83% of the funds, totaling 417,348 ETH (~$1 billion), were converted into BTC across 6,954 wallets (an average of 1.71 BTC per wallet). This and the coming week are critical for freezing the funds as they begin to clear through exchanges, OTC, and P2P platforms.
- 72% of the converted ETH (361,255 ETH or $0.9B) was transferred via ThorChain, which we can trace.
- 16% of the funds (79,655 ETH) went dark via ExCH, and Bybit is still awaiting a response from the service.
- 8% of the funds (40,233 ETH or $100M) were routed through the OKX Web3 proxy, of which 16,680 ETH can be traced, while 23,553 ETH (~$65M) remain untraceable.
Bounty Program Updates:
- 11 participants helped freeze funds, with the top 3 players being Mantle, Paraswap, and ZachXBT.
- $2,178,797 USDT has been paid out to 11 bounty hunters.
Full details are available on LazarusBounty.com.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Update from Bybit CEO Ben Zhou on the Hack Investigation and Fund Freezing
The hackers have finished laundering all 499,000 ETH ($1.39 billion) stolen from Bybit in just 10 days. The main channel used for laundering the funds was THORChain, which processed transactions totaling $5.9 billion and earned $5.5 million in handling fees. Incredible numbers!
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

The platform now provides details about the bridges through which the funds were transferred, including ThorChain (the main channel), OKX Web3 Proxy, Maya Protoco, Li.fi, and Transit Swap.
It is worth noting that only OKX Web3 Proxy did not respond to Bybit, and through this bridge, over $70 million worth of funds have been moved, which remain untraceable to this day.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
It is worth noting that only OKX Web3 Proxy did not respond to Bybit, and through this bridge, over $70 million worth of funds have been moved, which remain untraceable to this day.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

Updates on LazarusBounty.com: new data on cryptocurrency bridges used to move stolen funds from Bybit
Recently, a proposal allegedly from Bybit appeared on the Paraswap platform, asking for the return of 44.67 wETH (about $92 000) that was collected through Paraswap as transaction fees during the exchange of stolen funds from Bybit. The hackers used Paraswap to launder a portion of the stolen assets, and now the platform has been asked to return these funds for asset recovery.
However, doubts have been raised about the authenticity of this proposal. The address to which the funds are to be sent — 0x3ac32a00afb4ca177a0e1b6899ab90d0b811412f — is empty and has no transactions, which casts doubt on its connection to the real Bybit.
Participants of the Paraswap DAO have expressed concerns that this request may be from hackers, not an official Bybit representative. Some believe that Paraswap, as a decentralized service, should not be responsible for the security of centralized platforms and that returning funds simply because they were used in illicit transactions could set a dangerous precedent.
In response to these issues, the platform is discussing various factors, ranging from ethical concerns to potential legal consequences. Some propose returning a portion of the funds as compensation for processing costs, while others question the appropriateness of intervening without clear legal grounds.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
However, doubts have been raised about the authenticity of this proposal. The address to which the funds are to be sent — 0x3ac32a00afb4ca177a0e1b6899ab90d0b811412f — is empty and has no transactions, which casts doubt on its connection to the real Bybit.
Participants of the Paraswap DAO have expressed concerns that this request may be from hackers, not an official Bybit representative. Some believe that Paraswap, as a decentralized service, should not be responsible for the security of centralized platforms and that returning funds simply because they were used in illicit transactions could set a dangerous precedent.
In response to these issues, the platform is discussing various factors, ranging from ethical concerns to potential legal consequences. Some propose returning a portion of the funds as compensation for processing costs, while others question the appropriateness of intervening without clear legal grounds.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Recently, a proposal allegedly from Bybit appeared on the Paraswap platform, asking for the return of 44.67 wETH (about $92 000) that was collected through Paraswap as transaction fees during the exchange of stolen funds from Bybit. The hackers used Paraswap to launder a portion of the stolen assets, and now the platform has been asked to return these funds for asset recovery.
However, doubts have been raised about the authenticity of this proposal. The address to which the funds are to be sent — 0x3ac32a00afb4ca177a0e1b6899ab9
0d0b811412f — is empty and has no transactions, which casts doubt on its connection to the real Bybit.
Participants of the Paraswap DAO have expressed concerns that this request may be from hackers, not an official Bybit representative. Some believe that Paraswap, as a decentralized service, should not be responsible for the security of centralized platforms and that returning funds simply because they were used in illicit transactions could set a dangerous precedent.
In response to these issues, the platform is discussing various factors, ranging from ethical concerns to potential legal consequences. Some propose returning a portion of the funds as compensation for processing costs, while others question the appropriateness of intervening without clear legal grounds.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
However, doubts have been raised about the authenticity of this proposal. The address to which the funds are to be sent — 0x3ac32a00afb4ca177a0e1b6899ab9
0d0b811412f — is empty and has no transactions, which casts doubt on its connection to the real Bybit.
Participants of the Paraswap DAO have expressed concerns that this request may be from hackers, not an official Bybit representative. Some believe that Paraswap, as a decentralized service, should not be responsible for the security of centralized platforms and that returning funds simply because they were used in illicit transactions could set a dangerous precedent.
In response to these issues, the platform is discussing various factors, ranging from ethical concerns to potential legal consequences. Some propose returning a portion of the funds as compensation for processing costs, while others question the appropriateness of intervening without clear legal grounds.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

The situation with returning stolen funds via Paraswap: a proposal from "Bybit" or hackers?
*Legend on the link graph:
⚫️ - Bitcoin network attacker addresses
🟠 - Thorchain bridge addresses that provided liquidity to the Bitcoin network from the Ethereum network
From March 3–4, 2025, the perpetrators behind the Bybit Exploit moved to a new stage of laundering the stolen funds. Transactions were detected on the Bitcoin network that distributed funds to multiple addresses in a single transaction. Further complicating the tracking is the fact that these transactions involve multiple senders. This makes it extremely difficult to match specific inputs to corresponding outputs, making it much more difficult to analyze and track the further movement of the stolen assets.
The graph shows the flow of funds from Thorchain addresses in the Bitcoin network, which the attackers used to transfer liquidity from the Ethereum network to the Bitcoin network.
Up until now, the attackers used the simplest transactions in the Bitcoin network, which involve 1 sender and 1 recipient. Such transactions can be interpreted as a transfer of funds from the sender to the recipient. Starting from March 3-4, new transactions were noticed, where multiple senders send funds to multiple addresses.
Such transactions should be called Aggregated Transaction.
Aggregated Transaction - when a transaction combines inputs from multiple sources and distributes them across multiple outputs, but not for privacy reasons (unlike CoinJoin). This should not be confused with a Coinjoin transaction, as CoinJoin is designed specifically for privacy reasons. Multiple users combine their transactions to confuse blockchain analysis, and the outputs usually have the same amounts, which is not the case in the attacker's transactions under investigation.
It is noteworthy that the Lazarus group uses blockchain addresses in the process of laundering funds, where the cryptocurrency was stored for more than a year.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
⚫️ - Bitcoin network attacker addresses
🟠 - Thorchain bridge addresses that provided liquidity to the Bitcoin network from the Ethereum network
From March 3–4, 2025, the perpetrators behind the Bybit Exploit moved to a new stage of laundering the stolen funds. Transactions were detected on the Bitcoin network that distributed funds to multiple addresses in a single transaction. Further complicating the tracking is the fact that these transactions involve multiple senders. This makes it extremely difficult to match specific inputs to corresponding outputs, making it much more difficult to analyze and track the further movement of the stolen assets.
The graph shows the flow of funds from Thorchain addresses in the Bitcoin network, which the attackers used to transfer liquidity from the Ethereum network to the Bitcoin network.
Up until now, the attackers used the simplest transactions in the Bitcoin network, which involve 1 sender and 1 recipient. Such transactions can be interpreted as a transfer of funds from the sender to the recipient. Starting from March 3-4, new transactions were noticed, where multiple senders send funds to multiple addresses.
Such transactions should be called Aggregated Transaction.
Aggregated Transaction - when a transaction combines inputs from multiple sources and distributes them across multiple outputs, but not for privacy reasons (unlike CoinJoin). This should not be confused with a Coinjoin transaction, as CoinJoin is designed specifically for privacy reasons. Multiple users combine their transactions to confuse blockchain analysis, and the outputs usually have the same amounts, which is not the case in the attacker's transactions under investigation.
It is noteworthy that the Lazarus group uses blockchain addresses in the process of laundering funds, where the cryptocurrency was stored for more than a year.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

Lazarus Group moves to next laundering step
According to the analysis of attacks by Lazarus Group, the cybercriminals have extensive experience and tools to launder stolen funds.
In March 2022, they carried out the largest hack in crypto history, stealing more than $620 million from the cross-chain bridge Ronin Bridge. This incident was part of a larger trend of attacks on DeFi protocols, especially cross-chain bridges.
Almost immediately after the attack, Lazarus began transferring the stolen funds to Tornado Cash, using this mixer to subsequently launder them and cover their tracks.
These actions confirm that the group has deep knowledge of blockchain anonymization and continues to refine their methods of evading surveillance.
It is noteworthy that the Lazarus group uses blockchain addresses in the process of laundering funds where the cryptocurrency has been stored for more than a year. This may indicate several important aspects of their strategy:
1. Use of "dormant" funds
The use of old addresses that have remained inactive for a long time may be part of a well-thought-out scheme. Such funds may have belonged to Lazarus since previous attacks or were acquired through third parties, which makes them more difficult to trace.
2. Connection to previous incidents
The fact that old funds are involved in the laundering process may indicate their connection to earlier cybercrimes. Perhaps these assets are part of previously stolen funds that were stored for a long time for later use.
3. Cold Mixing Technique
Lazarus may have prepared these funds in advance, waiting for the right moment to move them and mix them with new flows of stolen assets. This method reduces the likelihood of identifying links between different attacks.
4. Breaking Trails and Complicating Analysis
Involving old funds in new transactions creates additional obstacles for analysts and blockchain monitoring systems. It makes it difficult to automatically determine the origin of assets and can confuse algorithms focused on analyzing recent transactions.
5. Possible Use of "Sleeping" Funds
Lazarus may have distributed funds to "dormant" wallets in advance, counting on the fact that investigators would not be interested in these addresses. After a long period of inactivity, such funds may be perceived as "forgotten" or "abandoned", making their sudden movement less obvious.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
In March 2022, they carried out the largest hack in crypto history, stealing more than $620 million from the cross-chain bridge Ronin Bridge. This incident was part of a larger trend of attacks on DeFi protocols, especially cross-chain bridges.
Almost immediately after the attack, Lazarus began transferring the stolen funds to Tornado Cash, using this mixer to subsequently launder them and cover their tracks.
These actions confirm that the group has deep knowledge of blockchain anonymization and continues to refine their methods of evading surveillance.
It is noteworthy that the Lazarus group uses blockchain addresses in the process of laundering funds where the cryptocurrency has been stored for more than a year. This may indicate several important aspects of their strategy:
1. Use of "dormant" funds
The use of old addresses that have remained inactive for a long time may be part of a well-thought-out scheme. Such funds may have belonged to Lazarus since previous attacks or were acquired through third parties, which makes them more difficult to trace.
2. Connection to previous incidents
The fact that old funds are involved in the laundering process may indicate their connection to earlier cybercrimes. Perhaps these assets are part of previously stolen funds that were stored for a long time for later use.
3. Cold Mixing Technique
Lazarus may have prepared these funds in advance, waiting for the right moment to move them and mix them with new flows of stolen assets. This method reduces the likelihood of identifying links between different attacks.
4. Breaking Trails and Complicating Analysis
Involving old funds in new transactions creates additional obstacles for analysts and blockchain monitoring systems. It makes it difficult to automatically determine the origin of assets and can confuse algorithms focused on analyzing recent transactions.
5. Possible Use of "Sleeping" Funds
Lazarus may have distributed funds to "dormant" wallets in advance, counting on the fact that investigators would not be interested in these addresses. After a long period of inactivity, such funds may be perceived as "forgotten" or "abandoned", making their sudden movement less obvious.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

Lazarus Group appears to have extensive experience and tools to launder funds
DAY 13. 2025-03-05
Today, Bybit CEO Ben Zhou thanked Hong Fang, President of OKX, for their assistance in reducing the untraceable stolen funds from Bybit. In his tweet, Ben stated that, following active cooperation with OKX's team, the untraceable amount had been reduced to 3985 ETH, and they will continue working together to further lower this figure.
Hong Fang emphasized that OKX is actively updating blacklist addresses and that all transactions in self-custody wallets should be traceable. He also suggested centralizing requests via email (safety@okx.com) to ensure more efficient communication and offered help from OKX's Web3 team in analyzing chains and bridges to trace the funds.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
Hong Fang emphasized that OKX is actively updating blacklist addresses and that all transactions in self-custody wallets should be traceable. He also suggested centralizing requests via email (safety@okx.com) to ensure more efficient communication and offered help from OKX's Web3 team in analyzing chains and bridges to trace the funds.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist


Bybit and OKX's Response to the Hack: Collaboration to Reduce Untraceable Funds
On February 21, 2025, the cryptocurrency exchange Bybit fell victim to the largest hack in the history of crypto, amounting to $1.4 billion. This incident was a true test for Ben Zhou, CEO and co-founder of Bybit, who found himself at the center of a crisis requiring immediate decisions and a swift response. Such situations can either strengthen or damage a leader’s reputation. Here’s how Bybit and Ben Zhou tackled this challenge:
Ben Zhou, co-founder and CEO of Bybit, previously worked in the financial sector, and in 2018, he founded Bybit, which quickly became one of the world’s largest cryptocurrency platforms. His experience in the financial industry helped him navigate the crisis, but the hack incident has undoubtedly been an important lesson for the entire industry.
This situation highlights the importance of crisis management, constant readiness for attacks, and the need for transparency and cooperation between platforms, analytics firms, and law enforcement agencies in handling major incidents.
The information is based on an article on Cointelegraph, thanks to the author for providing the data. The full version and all details can be found at this link.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
- Immediate Response: Upon learning of the hack, Ben Zhou took charge right away and began responding within 30 minutes. He actively used his X account and organized a two-hour live stream, providing real-time updates and reassuring users.
- Platform Continuity: Despite the crisis, Bybit continued to offer its services, including withdrawals, processing more than 350,000 requests within the first 12 hours after the hack.
- Securing Emergency Funding: The exchange secured emergency funding and successfully replenished its asset reserves, maintaining a 1:1 ratio to protect customer funds.
- Industry Support: In response to the incident, competing cryptocurrency exchanges and other industry players joined forces with Bybit, identifying and blocking hacker addresses, and helping to prevent further movement of the stolen funds.
- Independent Audit: To ensure transparency and financial stability, Bybit enlisted Hacken to conduct a reserves audit, confirming that all assets were fully backed 1:1.
- Collaboration with Law Enforcement: In response to the incident, Bybit actively collaborated with law enforcement, which helped provide a swift and effective response to the breach.
- Ben Zhou’s Response: Ben Zhou not only responded swiftly to the hack but also actively shared information with users and investors, building their trust.
- User Support: Within 12 hours of the hack, more than 350,000 withdrawal requests were processed, and the exchange continued to operate normally, providing users access to their assets.
Ben Zhou, co-founder and CEO of Bybit, previously worked in the financial sector, and in 2018, he founded Bybit, which quickly became one of the world’s largest cryptocurrency platforms. His experience in the financial industry helped him navigate the crisis, but the hack incident has undoubtedly been an important lesson for the entire industry.
This situation highlights the importance of crisis management, constant readiness for attacks, and the need for transparency and cooperation between platforms, analytics firms, and law enforcement agencies in handling major incidents.
The information is based on an article on Cointelegraph, thanks to the author for providing the data. The full version and all details can be found at this link.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
How Ben Zhou and Bybit Handled the Largest $1.4 Billion Hack
The AML Crypto team conducted an investigation into the Bybit exploit incident on the Arbitrum network. The investigation began with addresses verified by the LazarusBounty website, which is affiliated with the Bybit team.
*Legend on the graph:
🟣 - decentralized and centralized addresses
⚫️ - Bybit exploiter addresses
🟠 - bridge and centralized services addresses
🔴 - verified Bybit exploiter addresses by Bybit
Full-size graph
During the investigation, new tactics used by malicious actors were identified, revealing sophisticated schemes for concealing the movement of illicit funds. Analysis of the behavior of involved addresses showed that, on most addresses linked to the Bybit exploit, the perpetrator actively employs Thorchain Staking. This method not only helps obscure the origin of assets but also effectively mixes them with legitimate flows, significantly complicating the tracking and analysis of the transaction chain.
Staking is the process of locking up cryptocurrency to support the operation of a blockchain and earn rewards. It is available in networks that use Proof-of-Stake (PoS) and its variations.
Additionally, it was established that a significant portion of the funds obtained through attacks was transferred to the Arbitrum network using services such as Maya Protocol, Chainflip, Unizen Pro, and Cow Protocol. These platforms facilitate the rapid movement of assets across different blockchains, making them a convenient tool for obscuring the traces of illicit transactions.
After passing through a series of transit addresses, the funds continue moving and are withdrawn through OKX DEX, Across Protocol, and Maya Protocol into various networks. The majority of these funds are directed into the Ethereum ecosystem, which may indicate further attempts to integrate them into legitimate financial flows via decentralized exchanges, staking platforms, or mixing services.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
*Legend on the graph:
🟣 - decentralized and centralized addresses
⚫️ - Bybit exploiter addresses
🟠 - bridge and centralized services addresses
🔴 - verified Bybit exploiter addresses by Bybit
Full-size graph
During the investigation, new tactics used by malicious actors were identified, revealing sophisticated schemes for concealing the movement of illicit funds. Analysis of the behavior of involved addresses showed that, on most addresses linked to the Bybit exploit, the perpetrator actively employs Thorchain Staking. This method not only helps obscure the origin of assets but also effectively mixes them with legitimate flows, significantly complicating the tracking and analysis of the transaction chain.
Staking is the process of locking up cryptocurrency to support the operation of a blockchain and earn rewards. It is available in networks that use Proof-of-Stake (PoS) and its variations.
Additionally, it was established that a significant portion of the funds obtained through attacks was transferred to the Arbitrum network using services such as Maya Protocol, Chainflip, Unizen Pro, and Cow Protocol. These platforms facilitate the rapid movement of assets across different blockchains, making them a convenient tool for obscuring the traces of illicit transactions.
After passing through a series of transit addresses, the funds continue moving and are withdrawn through OKX DEX, Across Protocol, and Maya Protocol into various networks. The majority of these funds are directed into the Ethereum ecosystem, which may indicate further attempts to integrate them into legitimate financial flows via decentralized exchanges, staking platforms, or mixing services.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

Bybit Exploit Incident: Arbitrum Network Transactions
The investigation began with addresses verified on the Lazarus Bounty website. Major fund flows associated with the attacker’s addresses in the BSC network were analyzed.
*Legend on the graph №1
⚫️ - addresses affiliated with Bybit exploiter
🟠 - bridges addresses
🟣 - dex addresses
During the investigation, it was discovered that the attackers use a method of looping funds through specific addresses. These addresses can be conditionally divided into HOP levels, which represent transaction stages based on their position in the chain. When the funds reach the final HOP level, the attacker sends them back to HOP-1, after which they pass through all levels again, but in a different sequence.
To visually illustrate this process, the AMLCrypto.io team has prepared a simplified visualization of fund movements:
*Legend on the graph №2
⚫️ - addresses affiliated with Bybit exploiter
🟠 - bridges addresses
For the investigation, the address 0x9c249b3db6345367b43b2ced4c07d4ffa1fb5e11, verified by LazarusBounty, was analyzed. This address received [201,216 USDC from the Ethereum network]. The funds moved through more than 40 transactions, looping between 33 addresses before being withdrawn to OKX DEX.
Below is a simplified visualization of the fund looping scheme used by the attacker in the Binance Smart Chain network.
Explanation of the Video:
🟠 Orange paths illustrate the movement of funds from the Ethereum network to the OKX DEX service.
🔵 Blue paths represent branches along this route. They show one of the possible ways funds move through multiple attacker-controlled addresses before reaching OKX DEX. In the blockchain, these blue paths are formed for each attacker’s address involved in the scheme.
A notable pattern is the periodic splitting of the fund flow into multiple addresses by the attacker. At certain points, funds are simultaneously held across multiple addresses before being transferred further down the chain. All these transactions occur within the same second, indicating a high level of automation and ruling out the possibility of manual fund transfers.
*Legend on the graph №1
⚫️ - addresses affiliated with Bybit exploiter
🟠 - bridges addresses
🟣 - dex addresses
During the investigation, it was discovered that the attackers use a method of looping funds through specific addresses. These addresses can be conditionally divided into HOP levels, which represent transaction stages based on their position in the chain. When the funds reach the final HOP level, the attacker sends them back to HOP-1, after which they pass through all levels again, but in a different sequence.
To visually illustrate this process, the AMLCrypto.io team has prepared a simplified visualization of fund movements:
*Legend on the graph №2
⚫️ - addresses affiliated with Bybit exploiter
🟠 - bridges addresses
For the investigation, the address 0x9c249b3db6345367b43b2ced4c07d4ffa1fb5e11, verified by LazarusBounty, was analyzed. This address received [201,216 USDC from the Ethereum network]. The funds moved through more than 40 transactions, looping between 33 addresses before being withdrawn to OKX DEX.
Below is a simplified visualization of the fund looping scheme used by the attacker in the Binance Smart Chain network.
Explanation of the Video:
🟠 Orange paths illustrate the movement of funds from the Ethereum network to the OKX DEX service.
🔵 Blue paths represent branches along this route. They show one of the possible ways funds move through multiple attacker-controlled addresses before reaching OKX DEX. In the blockchain, these blue paths are formed for each attacker’s address involved in the scheme.
A notable pattern is the periodic splitting of the fund flow into multiple addresses by the attacker. At certain points, funds are simultaneously held across multiple addresses before being transferred further down the chain. All these transactions occur within the same second, indicating a high level of automation and ruling out the possibility of manual fund transfers.
The investigation began with addresses verified on the Lazarus Bounty website. Major fund flows associated with the attacker’s addresses in the BSC network were analyzed.
*Legend on the graph №1
⚫️ - addresses affiliated with Bybit exploiter
🟠 - bridges addresses
🟣 - dex addresses
During the investigation, it was discovered that the attackers use a method of looping funds through specific addresses. These addresses can be conditionally divided into HOP levels, which represent transaction stages based on their position in the chain. When the funds reach the final HOP level, the attacker sends them back to HOP-1, after which they pass through all levels again, but in a different sequence.
To visually illustrate this process, the AMLCrypto.io team has prepared a simplified visualization of fund movements:
*Legend on the graph №2
⚫️ - addresses affiliated with Bybit exploiter
🟠 - bridges addresses
For the investigation, the address 0x9c249b3db6345367b43b2ced4c07
d4ffa1fb5e11, verified by LazarusBounty, was analyzed. This address received [201,216 USDC from the Ethereum network]. The funds moved through more than 40 transactions, looping between 33 addresses before being withdrawn to OKX DEX.
Below is a simplified visualization of the fund looping scheme used by the attacker in the Binance Smart Chain network.
Explanation of the Video:
🟠 Orange paths illustrate the movement of funds from the Ethereum network to the OKX DEX service.
🔵 Blue paths represent branches along this route. They show one of the possible ways funds move through multiple attacker-controlled addresses before reaching OKX DEX. In the blockchain, these blue paths are formed for each attacker’s address involved in the scheme.
A notable pattern is the periodic splitting of the fund flow into multiple addresses by the attacker. At certain points, funds are simultaneously held across multiple addresses before being transferred further down the chain. All these transactions occur within the same second, indicating a high level of automation and ruling out the possibility of manual fund transfers.
*Legend on the graph №1
⚫️ - addresses affiliated with Bybit exploiter
🟠 - bridges addresses
🟣 - dex addresses
During the investigation, it was discovered that the attackers use a method of looping funds through specific addresses. These addresses can be conditionally divided into HOP levels, which represent transaction stages based on their position in the chain. When the funds reach the final HOP level, the attacker sends them back to HOP-1, after which they pass through all levels again, but in a different sequence.
To visually illustrate this process, the AMLCrypto.io team has prepared a simplified visualization of fund movements:
*Legend on the graph №2
⚫️ - addresses affiliated with Bybit exploiter
🟠 - bridges addresses
For the investigation, the address 0x9c249b3db6345367b43b2ced4c07
d4ffa1fb5e11, verified by LazarusBounty, was analyzed. This address received [201,216 USDC from the Ethereum network]. The funds moved through more than 40 transactions, looping between 33 addresses before being withdrawn to OKX DEX.
Below is a simplified visualization of the fund looping scheme used by the attacker in the Binance Smart Chain network.
Explanation of the Video:
🟠 Orange paths illustrate the movement of funds from the Ethereum network to the OKX DEX service.
🔵 Blue paths represent branches along this route. They show one of the possible ways funds move through multiple attacker-controlled addresses before reaching OKX DEX. In the blockchain, these blue paths are formed for each attacker’s address involved in the scheme.
A notable pattern is the periodic splitting of the fund flow into multiple addresses by the attacker. At certain points, funds are simultaneously held across multiple addresses before being transferred further down the chain. All these transactions occur within the same second, indicating a high level of automation and ruling out the possibility of manual fund transfers.


The AMLCrypto.io team conducted an investigation into the Bybit exploit incident on the Binance Smart Chain network.
Ben Zhou, CEO of ByBit, has shared new details regarding the investigation into the largest cryptocurrency hack, valued at $1.4 billion. The hackers involved in the incident have started actively using mixers to conceal the stolen funds:
🔑 Key Points:
- Hackers have begun using mixers: Wasabi, CryptoMixer, Railgun, TornadoCash.
- 88.87% of the funds remain traceable, 7.59% have gone "dark," and 3.54% have been frozen.
- 86.29% of the funds (440,091 ETH, approximately $1.23B) have been converted into 12,836 BTC, spread across 9,117 wallets (average 1.41 BTC per wallet).
- A portion of the funds (193 BTC) was sent through Wasabi Mixer, then transferred via various P2P platforms.
💡 The Mixer Problem: Currently, the most challenging task is decoding transactions that have passed through mixers. This requires significant efforts, and the ByBit team is urging bounty hunters to assist in analyzing these transactions.
Forecast: As hackers continue to use mixers, the number of such transactions will grow. Therefore, it is crucial to involve more experts and bounty hunters capable of decoding this data for the investigation.
The ByBit team is calling on anyone who can help with the investigation to reach out via Lazarus Bounty.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist
🔑 Key Points:
- Hackers have begun using mixers: Wasabi, CryptoMixer, Railgun, TornadoCash.
- 88.87% of the funds remain traceable, 7.59% have gone "dark," and 3.54% have been frozen.
- 86.29% of the funds (440,091 ETH, approximately $1.23B) have been converted into 12,836 BTC, spread across 9,117 wallets (average 1.41 BTC per wallet).
- A portion of the funds (193 BTC) was sent through Wasabi Mixer, then transferred via various P2P platforms.
💡 The Mixer Problem: Currently, the most challenging task is decoding transactions that have passed through mixers. This requires significant efforts, and the ByBit team is urging bounty hunters to assist in analyzing these transactions.
Forecast: As hackers continue to use mixers, the number of such transactions will grow. Therefore, it is crucial to involve more experts and bounty hunters capable of decoding this data for the investigation.
The ByBit team is calling on anyone who can help with the investigation to reach out via Lazarus Bounty.
API for getting the blacklist: https://btrace.amlcrypto.io/api/v2/bybit_blacklist

New Data on the ByBit Hack as of March 20: Hackers Begin Using Mixers to Launder Funds
Want to learn more and get expert advice? Leave your email and we will contact you promptly!
Check blockchain address using Btrace
In seconds, determine the risk level of the counterparty’s address, find out the source of his funds and make an informed decision about interacting with him.

PREVENT FUNDS BLOCKING

PROTECT YOURSELF FROM SCAMMERS

AVOID TROUBLE WITH THE LAW
We also recommend













